Outbound dynamic NAT configuration example (non-overlapping addresses)
Network requirements
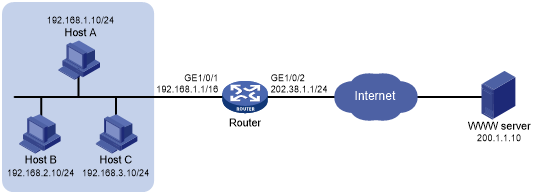
As shown in Figure 57, a company has a private address 192.168.0.0/16 and two public IP addresses 202.38.1.2 and 202.38.1.3. Configure outbound dynamic NAT to allow only internal users on subnet 192.168.1.0/24 to access the Internet.
Figure 57: Network diagram
Configuration procedure
# Specify IP addresses for the interfaces on the router. (Details not shown.)
# Configure address group 0, and add an address range from 202.38.1.2 to 202.38.1.3 to the group.
<Router> system-view [Router] nat address-group 0 [Router-address-group-0] address 202.38.1.2 202.38.1.3 [Router-address-group-0] quit
# Configure ACL 2000, and create a rule to permit packets only from subnet 192.168.1.0/24 to pass through.
[Router] acl basic 2000 [Router-acl-ipv4-basic-2000] rule permit source 192.168.1.0 0.0.0.255 [Router-acl-ipv4-basic-2000] quit
# Enable outbound dynamic PAT on interface GigabitEthernet 1/0/2. The source IP addresses of the packets permitted by the ACL rule is translated into the addresses in address group 0.
[Router] interface gigabitethernet 1/0/2 [Router-GigabitEthernet1/0/2] nat outbound 2000 address-group 0
Verifying the configuration
# Verify that Host A can access the WWW server, while Host B cannot. (Details not shown.)
# Display all NAT configuration and statistics.
[Router] display nat all
NAT address group information:
Totally 1 NAT address groups.
Address group 0:
Port range: 1-65535
Address information:
Start address End address
202.38.1.2 202.38.1.3
NAT outbound information:
Totally 1 NAT outbound rules.
Interface: GigabitEthernet1/0/2
ACL: 2000
Address group ID: 0
Port-preserved: N NO-PAT: N Reversible: N
Config status: Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NAT mapping behavior:
Mapping mode : Address and Port-Dependent
ACL : ---
Config status: Active
NAT ALG:
DNS : Enabled
FTP : Enabled
H323 : Enabled
ICMP-ERROR : Enabled
ILS : Enabled
MGCP : Enabled
NBT : Enabled
PPTP : Enabled
RSH : Enabled
RTSP : Enabled
SCCP : Enabled
SIP : Enabled
SQLNET : Enabled
TFTP : Enabled
XDMCP : Enabled
# Display NAT session information generated when Host A accesses the WWW server.
[Router] display nat session verbose Initiator: Source IP/port: 192.168.1.10/52992 Destination IP/port: 200.1.1.10/2048 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/1 Responder: Source IP/port: 200.1.1.10/4 Destination IP/port: 202.38.1.3/0 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/2 State: ICMP_REPLY Application: INVALID Start time: 2012-08-15 14:53:29 TTL: 12s Initiator->Responder: 1 packets 84 bytes Responder->Initiator: 1 packets 84 bytes Total sessions found: 1