Outbound bidirectional NAT configuration example
Network requirements
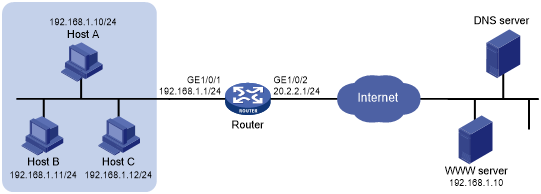
As shown in Figure 58, the private network where the Web server resides overlaps with the company private network 192.168.1.0/24. The company has two public IP addresses 202.38.1.2 and 202.38.1.3. Configure NAT to allow internal users to access the external Web server by using the server's domain name.
Figure 58: Network diagram
Requirements analysis
To meet the network requirements, you must perform the following tasks:
Configure inbound dynamic NAT with ALG to make sure the internal host reaches the Web server instead of another internal host. NAT with ALG can translate the Web server's IP address in the DNS reply payload to a dynamically assigned public address.
Configure outbound dynamic NAT to translate the source IP address of packets from an internal host to a dynamically assigned public address.
Add a static route to the public IP address of the external Web server.
Configuration procedure
# Specify IP addresses for the interfaces on the router. (Details not shown.)
# Enable NAT with ALG and DNS.
<Router> system-view [Router] nat alg dns
# Configure ACL 2000, and create a rule to permit packets only from subnet 192.168.1.0/24 to pass through.
[Router] acl basic 2000 [Router-acl-ipv4-basic-2000] rule permit source 192.168.1.0 0.0.0.255 [Router-acl-ipv4-basic-2000] quit
# Create address group 1.
[Router] nat address-group 1
# Add address 202.38.1.2 to the group.
[Router-address-group-1] address 202.38.1.2 202.38.1.2 [Router-address-group-1] quit
# Create address group 2.
[Router] nat address-group 2
# Add address 202.38.1.3 to the group.
[Router-address-group-2] address 202.38.1.3 202.38.1.3 [Router-address-group-2] quit
# Enable inbound NO-PAT on interface GigabitEthernet 1/0/2 to translate the source IP address in the DNS reply payload into the address in address group 1, and allow reversible NAT.
[Router] interface gigabitethernet 1/0/2 [Router-GigabitEthernet1/0/2] nat inbound 2000 address-group 1 no-pat reversible
# Enable outbound PAT on interface GigabitEthernet 1/0/2 to translate the source address of outgoing packets into the address in address group 2.
[Router-GigabitEthernet1/0/2] nat outbound 2000 address-group 2
# Configure a static route to 202.38.1.2 with GigabitEthernet 1/0/2 as the output interface and 20.2.2.2 as the next hop. (The next hop address varies by network.)
[Router] ip route-static 202.38.1.2 32 gigabitethernet 1/0/2 20.2.2.2
Verifying the configuration
# Verify that Host A can access the Web server by using its domain name. (Details not shown.)
# Display all NAT configuration and statistics.
[Router] display nat all
NAT address group information:
Totally 2 NAT address groups.
Address group 1:
Port range: 1-65535
Address information:
Start address End address
202.38.1.2 202.38.1.2
Address group 2:
Port range: 1-65535
Address information:
Start address End address
202.38.1.3 202.38.1.3
NAT inbound information:
Totally 1 NAT inbound rules.
Interface: GigabitEthernet1/0/2
ACL: 2000
Address group ID: 1
Add route: N NO-PAT: Y Reversible: Y
NAT outbound information:
Totally 1 NAT outbound rules.
Interface: GigabitEthernet1/0/2
ACL: 2000
Address group ID: 2
Port-preserved: N NO-PAT: N Reversible: N
Config status: Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NAT mapping behavior:
Mapping mode : Address and Port-Dependent
ACL : ---
Config status: Active
NAT ALG:
DNS : Enabled
FTP : Enabled
H323 : Enabled
ICMP-ERROR : Enabled
ILS : Enabled
MGCP : Enabled
NBT : Enabled
PPTP : Enabled
RSH : Enabled
RTSP : Enabled
SCCP : Enabled
SIP : Enabled
SQLNET : Enabled
TFTP : Enabled
XDMCP : Enabled
# Display NAT session information generated when Host A accesses the Web server.
[Router] display nat session verbose Initiator: Source IP/port: 192.168.1.10/1694 Destination IP/port: 202.38.1.2/8080 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: TCP(6) Inbound interface: GigabitEthernet1/0/1 Responder: Source IP/port: 192.168.1.10/8080 Destination IP/port: 202.38.1.3/1025 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: TCP(6) Inbound interface: GigabitEthernet1/0/2 State: TCP_ESTABLISHED Application: HTTP Start time: 2012-08-15 14:53:29 TTL: 3597s Initiator->Responder: 7 packets 308 bytes Responder->Initiator: 5 packets 312 bytes Total sessions found: 1