Configuration example for LAC-auto-initiated VPN
Network requirements
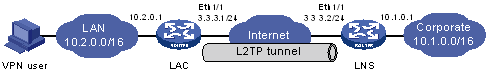
As shown in Figure 98, create a virtual PPP user on the LAC and configure the LAC to initiate a tunneling request to the LNS to establish an L2TP tunnel for the virtual PPP user. When a VPN user accesses the corporate network, all packets between the VPN user and the corporate network are transmitted through the L2TP tunnel.
A VPN user accesses the corporate network in the following procedure:
The VPN user sends a packet to the LAC through the LAN.
The LAC encapsulates the packet and then forwards the packet through the L2TP tunnel to the LNS.
Figure 98: Network diagram
Configuration procedure
Configure the LNS:
# Configure IP addresses for interfaces. (Details not shown.)
# Create a local user, configure a username and password for the user, and specify the service type as PPP.
<LNS> system-view [LNS] local-user vpdnuser [LNS-luser-vpdnuser] password simple Hello [LNS-luser-vpdnuser] service-type ppp [LNS-luser-vpdnuser] quit
# Configure a VT interface.
[LNS] interface virtual-template 1 [LNS-virtual-template1] ip address 192.168.0.20 255.255.255.0 [LNS-virtual-template1] remote address pool 1 [LNS-virtual-template1] ppp authentication-mode pap [LNS-virtual-template1] quit
# Configure local authentication for VPN users.
[LNS] domain system [LNS-isp-system] authentication ppp local [LNS-isp-system] ip pool 1 192.168.0.2 192.168.0.100 [LNS-isp-system] quit
# Enable L2TP and create an L2TP group.
[LNS] l2tp enable [LNS] l2tp-group 1
# Configure the local tunnel name and specify the VT interface for receiving packets and the tunnel name on the LAC.
[LNS-l2tp1] tunnel name LNS [LNS-l2tp1] allow l2tp virtual-template 1 remote LAC
# Enable tunnel authentication and configure the authentication key.
[LNS-l2tp1] tunnel authentication [LNS-l2tp1] tunnel password simple aabbcc [LNS-l2tp1] quit
# Configure a static route so that packets destined for the VPN will be forwarded through the L2TP tunnel.
[LNS] ip route-static 10.2.0.0 16 virtual-template 1
Configure the LAC:
# Configure IP addresses for the interfaces. (Details not shown.)
# Enable L2TP and create an L2TP group.
<LAC> system-view [LAC] l2tp enable [LAC] l2tp-group 1
# Configure the local tunnel name and specify the IP address of the tunnel peer (LNS).
[LAC-l2tp1] tunnel name LAC [LAC-l2tp1] start l2tp ip 3.3.3.2 fullusername vpdnuser
# Enable tunnel authentication and configure the authentication key.
[LAC-l2tp1] tunnel authentication [LAC-l2tp1] tunnel password simple aabbcc [LAC-l2tp1] quit
# Configure the PPP authentication method PAP, authentication username vpdnuser, and password Hello for the virtual PPP user.
[LAC] interface virtual-template 1 [LAC-Virtual-Template1] ip address ppp-negotiate [LAC-Virtual-Template1] ppp pap local-user vpdnuser password simple Hello [LAC-Virtual-Template1] ppp authentication-mode pap [LAC-Virtual-Template1] quit
# Configure a static route so that packets destined for the corporate will be forwarded through the L2TP tunnel.
[LAC] ip route-static 10.1.0.0 16 virtual-template 1
# Create a local user, configure the username and password, and specify the service type as PPP.
[LAC] local-user vpdnuser [LAC-luser-vpdnuser] password simple Hello [LAC-luser-vpdnuser] service-type ppp
# Trigger the LAC to establish an L2TP tunnel with the LNS.
[LAC] interface virtual-template 1 [LAC-virtual-template1] l2tp-auto-client enable
![[NOTE: ]](images/note.png) | NOTE: On each host connected to the LAC or LNS, configure the gateway as the LAC or LNS. | |
Verify the configuration:
# On the LNS, perform the display l2tp session command to view the established L2TP session.
[LNS] display l2tp session Total session = 1 LocalSID RemoteSID LocalTID 8279 6822 1
# On the LNS, perform the display l2tp tunnel command to view the established L2TP tunnel.
[LNS] display l2tp tunnel Total tunnel = 1 LocalTID RemoteTID RemoteAddress Port Sessions RemoteName 1 1 3.3.3.1 1701 1 LAC
# On the LNS, you should be able to ping 10.2.0.1, a private network address on the LAC side. This indicates that hosts on 10.2.0.0/16 and those on 10.1.0.0/16 can communicate with each other through the L2TP tunnel.
[LNS] ping -a 10.1.0.1 10.2.0.1 PING 10.2.0.1: 56 data bytes, press CTRL_C to break Reply from 10.2.0.1: bytes=56 Sequence=1 ttl=255 time=2 ms Reply from 10.2.0.1: bytes=56 Sequence=2 ttl=255 time=2 ms Reply from 10.2.0.1: bytes=56 Sequence=3 ttl=255 time=2 ms Reply from 10.2.0.1: bytes=56 Sequence=4 ttl=255 time=2 ms Reply from 10.2.0.1: bytes=56 Sequence=5 ttl=255 time=2 ms --- 10.2.0.1 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 2/2/2 ms