Syntax:
show port-access authenticator [port-list] [config|statistics|session-counters|vlan|clients]|[detailed]If you enter the
show port-access authenticatorcommand without an optional value, the following configuration information is displayed for all switch ports, or specified ports, that are enabled for 802.1X port-access authentication:
Port-access authenticator activated: Are any switch ports configured to operate as 802.1X authenticators using the
aaa port-access authenticatorcommand?YesorNoAllow RADIUS-assigned dynamic (GVRP) VLANs: Are RADIUS-assigned dynamic (GVRP-learned) VLANs supported for authenticated and unauthenticated client sessions on the switch?
YesorNoUntagged VLAN: VLAN ID number of the untagged VLAN used in client sessions. If the switch supports MAC-based (untagged) VLANs, MACbased is displayed to show that multiple untagged VLANs are configured for authentication sessions.
Tagged VLANs: Are tagged VLANs (statically configured or RADIUS-assigned) used for authenticated clients?
YesorNo
Yes – Client-specific CoS (Class of Service) values are applied to more than one authenticated client on the port.
No – No client-specific CoS values are applied to any authenticated client on the port.
<CoS value> – Numerical value of the CoS (802.1p priority) applied to inbound traffic from one authenticated client. For client-specific per-port CoS values, enter the
show port-access web-based clients detailedcommand.RADIUS ACL: Are RADIUS-assigned ACLs used for authenticated clients? Yes or No
Cntrl Dir: Direction in which flow of incoming and outgoing traffic is blocked on 802.1X-aware port that has not yet entered the authenticated state:
The show port-access authenticator command
HP Switch(config)# show port-access authenticator
Port Access Authenticator Status
Port-access authenticator activated [No] : Yes
Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : Yes
Auth Unauth Untagged Tagged % In RADIUS Cntrl
Port Clients Clients VLAN VLANs Port COS Limit ACL Dir
---- ------- -------- -------- ------ --------- ------ ------ -----
1 1 1 4006 Yes 77777777 No Yes both
2 2 0 MACbased No No No Yes both
3 4 0 1 Yes No No No both
The information displayed with the show port-access authenticator command for individual (config|statistics|session-counters|vlan|clients) options is described below.
Syntax:
Displays 802.1X port-access authenticator configuration settings, including:
802.1X configuration of ports that are enabled as 802.1X authenticators (See the syntax descriptions in Reconfigure settings for port-access. Use the
show runningcommand to view the currentclient-limitconfiguration available for switches.)You can display 802.1X port-access authenticator configuration for all switch ports or specified ports. 802.1X configuration information for ports that are not enabled as 802.1X authenticators is not displayed.
The show port-access authenticator config command
HP Switch(config)# show port-access authenticator config
Port Access Authenticator Configuration
Port-access authenticator activated [No] : Yes
Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No
| Re-auth Access Max Quiet TX Supplicant Server Cntrl
Port | Period Control Reqs Period Timeout Timeout Timeout Dir
---- + ------- -------- ----- ------- -------- ---------- -------- -----
1 | No Auto 2 60 30 30 30 both
2 | No Auto 2 60 30 30 30 in
Field table
| Field | Description |
|---|---|
| Port-access authenticator activated | Whether 802.1X authentication is enabled or disabled on specified port(s). |
| Port | Port number on switch. |
| Re-auth Period | Period of time (in seconds) after which clients connected to the port need to be reauthenticated. |
| Access Control |
Port’s authentication mode: Auto: Network access is allowed to any connected device that supports 802.1X authentication and provides valid 802.1X credentials. Authorized: Network access is allowed to any device connected to the port, regardless of whether it meets 802.1X criteria. Unauthorized: Network access is blocked to any device connected to the port, regardless of whether the device meets 802.1X criteria. |
| Max reqs | Number of authentication attempts that must time-out before authentication fails and the authentication session ends. |
| Quiet Period | Period of time (in seconds) during which the port does not try to acquire a supplicant. |
| TX Timeout | Period of time (in seconds) that the port waits to retransmit the next EAPOL PDU during an authentication session. |
| Supplicant Timeout | Period of time (in seconds) that the switch waits for a supplicant response to an EAP request. |
| Server Timeout | Period of time (in seconds) that the switch waits for a server response to an authentication request. |
| Cntrl Dir |
Direction in which flow of incoming and outgoing traffic is blocked on 802.1X-aware port that has not yet entered the authenticated state: Both: Incoming and outgoing traffic is blocked on port until authentication occurs. In: Only incoming traffic is blocked on port before authentication occurs. Outgoing traffic with unknown destination addresses is flooded on the unauthenticated 802.1X-aware port. |
Syntax:
Displays statistical information for all switch ports or specified ports that are enabled as 802.1X authenticators, including:
802.1X configuration information for ports that are not enabled as an 802.1X authenticators is not displayed.
The show port-access authenticator statistics command
HP Switch(config)# show port-access authenticator statistics Port Access Authenticator Statistics Port-access authenticator activated [No] : Yes Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No Source TX TX RX RX RX RX RX Port MAC address ReqId Req Star Logoff RespId Resp Errors ---- ------------- ----- ---- ----- ------ ------ ---- ------ 2 001560-b3ea48 1 0 0 0 0 0 0Syntax:
Displays information for active 802.1X authentication sessions on all switch ports or specified ports that are enabled as 802.1X authenticators, including:
802.1X frames received and transmitted on each port
Duration and status of active 802.1X authentication sessions (
in-progressorterminated)User name of 802.1X supplicant included in 802.1X response packets, configured with the
aaa port-access supplicant identity <commandusername>802.1X configuration information for ports that are not enabled as an 802.1X authenticators is not displayed.
The show port-access authenticator session-counters command
HP Switch(config)# show port-access authenticator session-counters Port Access Authenticator Session Counters Port-access authenticator activated [No] : Yes Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No Session Session Port Frames In Frames Out Time(sec.) Status User ---- ---------- ----------- ---------- ----------- ----- 2 45623 45623 20 in-progress bertSyntax:
Displays the following information on the VLANs configured for use in 802.1X port-access authentication on all switch ports, or specified ports, that are enabled as 802.1X authenticator:
802.1X configuration information for ports that are not enabled as an 802.1X authenticators is not displayed.
The show port-access authenticator vlan command
HP Switch(config)# show port-access authenticator vlan Port Access Authenticator VLAN Configuration Port-access authenticator activated [No] : Yes Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No Access Unauth Auth Port Control VLAN ID VLAN ID ---- -------- -------- -------- 2 Auto 0 0Syntax:
Displays the session status, name, and address for each 802.1X port-access-authenticated client on the switch. Multiple authenticated clients may be displayed for the same port. The IP address displayed is taken from the DHCP binding table (learned through the DHCP Snooping feature).
If DHCP snooping is not enabled on the switch, n/a (not available) is displayed for a client’s IP address.
If an 802.1X-authenticated client uses an IPv6 address, n/a - IPv6 is displayed.
If DHCP snooping is enabled but no MAC-to-IP address binding for a client is found in the DHCP binding table, n/a - no info is displayed.
The show port-access authenticator clients command output
Switch (config)# show port-access authenticator clients Port Access Authenticator Client Status Port Client Name MAC Address IP Address Session Status ----- ----------- ------------- --------------- -------------- 1 webuser1 001321-eb8063 192.192.192.192 Authenticated 1 webuser2 001560-b3ea48 n/a - no info Authenticating 1 webuser3 000000-111111 n/a - IPv6 Authenticating 3 webuser4 000000-111112 n/a AuthenticatingSyntax:
Displays detailed information on the status of 802.1X-authenticated client sessions on specified ports, including the matches the switch detects for individual ACEs configured with the cnt (counter) option in an ACL assigned to the port by a RADIUS server.
Output for the show port-access authenticator clients detailed command
Switch (config)# show port-access authenticator clients 5 detailed
Port Access Authenticator Client Status Detailed
Client Base Details :
Port : 5
Session Status : Open Session Time(sec) : 999999999
Frames In : 999999999 Frames Out : 99999999
Username : webuser1 MAC Address : 001321-eb8063
IP : 2001:fecd:ba23:cd1f:dcb1:1010:9234:4088
Access Policy Details :
COS Map : 70000000 In Limit % : 87
Untagged VLAN : 3096 Out Limit % : 100
Tagged VLANs : 1, 3, 5, 6, 334, 2066
RADIUS-ACL List :
deny in udp from any to 10.2.8.233 CNT
Hit Count: 10
permit in udp from any to 10.2.8.233 CNT
Hit Count: 17
deny in tcp from any to 10.2.8.233 CNT
Hit Count: 1
permit in tcp from any to 10.2.8.233 CNT
Hit Count: 11
permit in ip from any to any cnt
Hit Count: 42
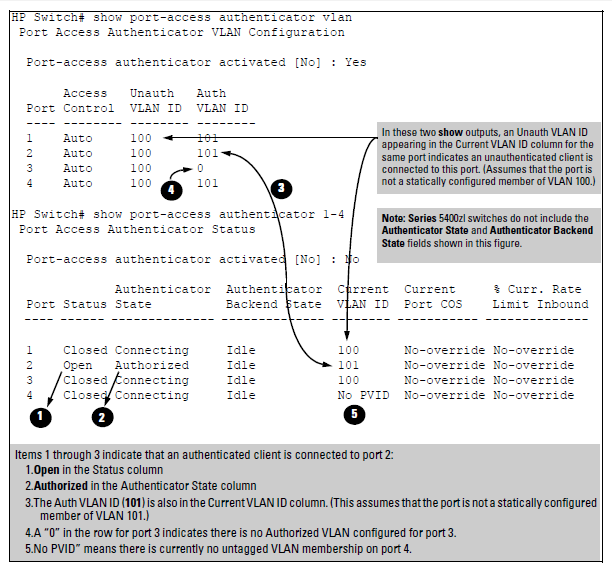
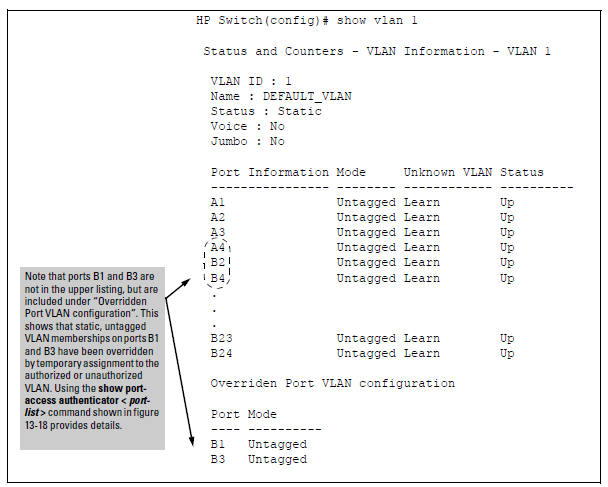
You can examine the switch’s current VLAN status by using the show port-access authenticator vlan and show port-access authenticator < commands as shown in Example showing ports configured for Open VLAN mode. Output for determining Open VLAN mode status describes the data that these two commands display. Example showing a VLAN with ports configured for Open VLAN mode shows related VLAN data that can help you to see how the switch is using statically configured VLANs to support 802.1X operation.port-list>
Thus, in the output shown in Example showing ports configured for Open VLAN mode:
-
When the Auth VLAN ID is configured and matches the Current VLAN ID, an authenticated client is connected to the port. (This assumes the port is not a statically configured member of the VLAN you are using for Auth VLAN.)
-
When the Unauth VLAN ID is configured and matches the Current VLAN ID, an unauthenticated client is connected to the port. (This assumes the port is not a statically configured member of the VLAN you are using for Unauth VLAN.)
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Because a temporary Open VLAN port assignment to either an authorized or unauthorized VLAN is an untagged VLAN membership, these assignments temporarily replace any other untagged VLAN membership that is statically configured on the port. For example, if port 12 is statically configured as an untagged member of VLAN 1, but is configured to use VLAN 25 as an authorized VLAN, then the port’s membership in VLAN 1 will be temporarily suspended whenever an authenticated 802.1X client is attached to the port. |
|
|
Output for determining Open VLAN mode status
| Status Indicator | Meaning |
|---|---|
| Access Control |
This state is controlled by the following port-access Command syntax: HP Switch(config)# aaa port-access authenticator <
Auto: Configures the port to allow network access to any connected device that supports 802.1X authentication and provides valid 802.1X credentials. (This is the default authenticator setting.) Authorized: Configures the port for “Force Authorized”, which allows access to any device connected to the port, regardless of whether it meets 802.1X criteria. (You can still configure console, Telnet, or SSH security on the port.) Unauthorized: Configures the port for “Force Unauthorized”, which blocks access to any device connected to the port, regardless of whether the device meets 802.1X criteria. |
| Unauthorized VLAN ID |
<vlan-id>: Lists the VID of the static VLAN configured as the unauthorized VLAN for the indicated port. 0: No unauthorized VLAN has been configured for the indicated port. |
| Authorized VLAN ID |
<vlan-id>: Lists the VID of the static VLAN configured as the authorized VLAN for the indicated port. 0: No authorized VLAN has been configured for the indicated port. |
| Status |
Closed: Either no client is connected or the connected client has not received authorization through 802.1X authentication. Open: An authorized 802.1X supplicant is connected to the port. |
| Current VLAN ID |
<vlan-id>: Lists the VID of the static, untagged VLAN to which the port currently belongs. No PVID: The port is not an untagged member of any VLAN. |
| Current Port CoS | See RADIUS Authentication, Authorization, and Accounting. |
| % Curr. Rate Limit Inbound |
Syntax:
Syntax:
Shows the port-access supplicant configuration (excluding the
secretparameter) for all ports or <> ports configured on the switch as supplicants. The Supplicant State can include the following:port-list
Connecting
Starting authentication.
Authenticated
Authentication completed (regardless of whether the attempt was successful).
Acquired
The port received a request for identification from an authenticator.
Authenticating
Authentication is in progress.
Held
Authenticator sent notice of failure. The supplicant port is waiting for the authenticator’s held-period.
For descriptions of the supplicant parameters, see Configuring a supplicant switch port.
Shows the port-access statistics and source MAC address(es) for all ports or <
> ports configured on the switch as supplicants. See Note on supplicant statistics.port-list
For each port configured as a supplicant, show port-access supplicant statistics < displays the source MAC address and statistics for transactions with the authenticator device most recently detected on the port. If the link between the supplicant port and the authenticator device fails, the supplicant port continues to show data received from the connection to the most recent authenticator device until one of the following occurs:port-list>]
-
The supplicant port detects a different authenticator device.
-
You use the
aaa port-access supplicant <command to clear the statistics for the supplicant port.port-list> clear-statistics -
The switch reboots.
Thus, if the supplicant’s link to the authenticator fails, the supplicant retains the transaction statistics it most recently received until one of the above events occurs. Also, if you move a link with an authenticator from one supplicant port to another without clearing the statistics data from the first port, the authenticator’s MAC address will appear in the supplicant statistics for both ports.