RBAC temporary user role authorization configuration example (RADIUS authentication)
Network requirements
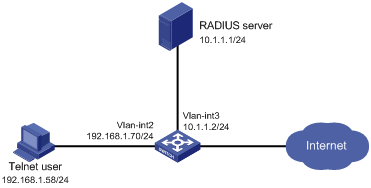
As shown in Figure 7, the switch uses local authentication for login users, including the Telnet user. The user account for the Telnet user is test@bbb and is assigned user role level-0.
Configure the remote-then-local authentication mode for temporary user role authorization. The switch uses the RADIUS server to provide authentication for the network-admin user role. If the AAA configuration is invalid or the RADIUS server does not respond, the switch performs local authentication.
Figure 7: Network diagram
Configuration procedure
Configure the switch:
# Assign an IP address to VLAN-interface 2 (the interface connected to the Telnet user).
<Switch> system-view [Switch] interface vlan-interface 2 [Switch-Vlan-interface2] ip address 192.168.1.70 255.255.255.0 [Switch-Vlan-interface2] quit
# Assign an IP address to VLAN-interface 3 (the interface connected to the RADIUS server).
[Switch] interface vlan-interface 3 [Switch-Vlan-interface3] ip address 10.1.1.2 255.255.255.0 [Switch-Vlan-interface3] quit
# Enable Telnet server.
[Switch] telnet server enable
# Enable scheme authentication on the user lines for Telnet users.
[Switch] line vty 0 63 [Switch-line-vty0-63] authentication-mode scheme [Switch-line-vty0-63] quit
# Enable remote-then-local authentication for temporary user role authorization.
[Switch] super authentication-mode scheme local
# Create RADIUS scheme radius and enter RADIUS scheme view.
[Switch] radius scheme radius
# Specify the primary authentication server address and the shared key in the scheme for secure communication between the switch and the server.
[Switch-radius-radius] primary authentication 10.1.1.1 key simple expert
# Exclude ISP domain names from the usernames sent to the RADIUS server.
[Switch-radius-radius] user-name-format without-domain [Switch-radius-radius] quit
# Create ISP domain bbb and enter ISP domain view.
[Switch] domain bbb
# Configure ISP domain bbb to use local authentication for login users.
[Switch-isp-bbb] authentication login local
# Configure ISP domain bbb to use local authorization for login users.
[Switch-isp-bbb] authorization login local
# Apply RADIUS scheme radius to the ISP domain for user role authentication.
[Switch-isp-bbb] authentication super radius-scheme radius [Switch-isp-bbb] quit
# Create a device management user named test and enter local user view.
[Switch] local-user test class manage
# Set the user service type to Telnet.
[Switch-luser-manage-test] service-type telnet
# Set the user password to aabbcc.
[Switch-luser-manage-test] password simple aabbcc
# Assign level-0 to the user.
[Switch-luser-manage-test] authorization-attribute user-role level-0
# Remove the default user role (network-operator).
[Switch-luser-manage-test] undo authorization-attribute user-role network-operator [Switch-luser-manage-test] quit
# Set the local authentication password to abcdef654321 for user role network-admin.
[Switch] super password role network-admin simple abcdef654321 [Switch] quit
Configure the RADIUS server:
This example uses ACSv4.2.
Add a user account named $enab0$ and set the password to 123456. (Details not shown.)
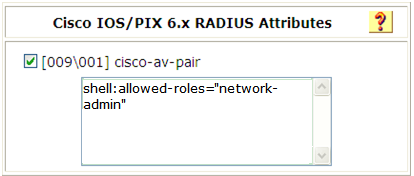
Access the Cisco IOS/PIX 6.x RADIUS Attributes page.
Configure the cisco-av-pair attribute, as shown in Figure 8.
Figure 8: Configuring the cisco-av-pair attribute
Verifying the configuration
Telnet to the switch, and enter username test@bbb and password aabbcc to access the switch. Verify that you have access to diagnostic commands.
<Switch> telnet 192.168.1.70 Trying 192.168.1.70 ... Press CTRL+K to abort Connected to 192.168.1.59 ... ****************************************************************************** * Copyright (c) 2010-2017 Hewlett Packard Enterprise Development LP * * Without the owner's prior written consent, * * no decompiling or reverse-engineering shall be allowed. * ****************************************************************************** login: test@bbb Password: <Switch>? User view commands: ping Ping function quit Exit from current command view ssh2 Establish a secure shell client connection super Switch to a user role system-view Enter the System View telnet Establish a telnet connection tracert Tracert function <switch>
Verify that you can obtain the network-admin user role:
# Use the super password to obtain the network-admin user role. When the system prompts for a username and password, enter username test@bbb and password 123456.
<Switch> super network-admin Username: test@bbb Password:
The following output shows that you have obtained the network-admin user role.
User privilege role is network-admin, and only those commands that authorized to the role can be used.
# If the ACS server does not respond, enter local authentication password abcdef654321 at the prompt.
Invalid configuration or no response from the authentication server. Change authentication mode to local. Password: User privilege role is network-admin, and only those commands that authorized to the role can be used.
The output shows that you have obtained the network-admin user role.