RBAC configuration example for RADIUS authentication users
Network requirements
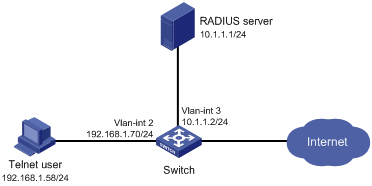
As shown in Figure 3, the switch uses the FreeRADIUS server to provide AAA service for login users, including the Telnet user. The user account for the Telnet user is hello@bbb and is assigned user role role2.
User role role2 has the following permissions:
Can use all commands in ISP view.
Can use the read and write commands of the arp and radius features.
Cannot access the read commands of the acl feature.
Can configure only VLANs 1 to 20 and interfaces Ten-GigabitEthernet 1/0/1 to Ten-GigabitEthernet 1/0/4.
The switch and the FreeRADIUS server use a shared key of expert and authentication port 1812. The switch delivers usernames with their domain names to the server.
Figure 3: Network diagram
Configuration procedure
Make sure the settings on the switch and the RADIUS server match.
Configure the switch:
# Assign VLAN-interface 2 an IP address from the same subnet as the Telnet user.
<Switch> system-view [Switch] interface vlan-interface 2 [Switch-Vlan-interface2] ip address 192.168.1.70 255.255.255.0 [Switch-Vlan-interface2] quit
# Assign VLAN-interface 3 an IP address from the same subnet as the RADIUS server.
[Switch] interface vlan-interface 3 [Switch-Vlan-interface3] ip address 10.1.1.2 255.255.255.0 [Switch-Vlan-interface3] quit
# Enable Telnet server.
[Switch] telnet server enable
# Enable scheme authentication on the user lines for Telnet users.
[Switch] line vty 0 63 [Switch-line-vty0-63] authentication-mode scheme [Switch-line-vty0-63] quit
# Create RADIUS scheme rad and enter RADIUS scheme view.
[Switch] radius scheme rad
# Specify the primary server address and the service port in the scheme.
[Switch-radius-rad] primary authentication 10.1.1.1 1812
# Set the shared key to expert in the scheme for the switch to authenticate to the server.
[Switch-radius-rad] key authentication simple expert [Switch-radius-rad] quit
# Specify scheme rad as the authentication and authorization schemes for ISP domain bbb.
![[IMPORTANT: ]](images/important.png)
IMPORTANT:
Because RADIUS user authorization information is piggybacked in authentication responses, the authentication and authorization methods must use the same RADIUS scheme.
[Switch] domain bbb [Switch-isp-bbb] authentication login radius-scheme rad [Switch-isp-bbb] authorization login radius-scheme rad [Switch-isp-bbb] quit
# Create feature group fgroup1.
[Switch] role feature-group name fgroup1
# Add the arp and radius features to the feature group.
[Switch-featuregrp-fgroup1] feature arp [Switch-featuregrp-fgroup1] feature radius [Switch-featuregrp-fgroup1] quit
# Create user role role2.
[Switch] role name role2
# Configure rule 1 to permit the user role to use all commands available in ISP view.
[Switch-role-role2] rule 1 permit command system-view ; domain *
# Configure rule 2 to permit the user role to use the read and write commands of all features in fgroup1.
[Switch-role-role2] rule 2 permit read write feature-group fgroup1
# Configure rule 3 to disable access to the read commands of the acl feature.
[Switch-role-role2] rule 3 deny read feature acl
# Configure rule 4 to permit the user role to create VLANs and use all commands available in VLAN view.
[Switch-role-role2] rule 4 permit command system-view ; vlan *
# Configure rule 5 to permit the user role to enter interface view and use all commands available in interface view.
[Switch-role-role2] rule 5 permit command system-view ; interface *
# Configure the user role VLAN policy to disable configuration of any VLAN except VLANs 1 to 20.
[Switch-role-role2] vlan policy deny [Switch-role-role2-vlanpolicy] permit vlan 1 to 20 [Switch-role-role2-vlanpolicy] quit
# Configure the user role interface policy to disable configuration of any interface except Ten-GigabitEthernet 1/0/1 to Ten-GigabitEthernet 1/0/4.
[Switch-role-role2] interface policy deny [Switch-role-role2-ifpolicy] permit interface ten-gigabitethernet 1/0/1 to ten-gigabitethernet 1/0/4 [Switch-role-role2-ifpolicy] quit [Switch-role-role2] quit
Configure the RADIUS server:
# Add either of the user role attributes to the dictionary file of the FreeRADIUS server.
Cisco-AVPair = "shell:roles=\"role2\"" Cisco-AVPair = "shell:roles*\"role2\""
# Configure the settings required for the FreeRADIUS server to communicate with the switch. (Details not shown.)
Verifying the configuration
# Telnet to the switch, and enter the username and password to access the switch. (Details not shown.)
# Verify that you can use all commands available in ISP view.
<Switch> system-view [Switch] domain abc [Switch-isp-abc] authentication login radius-scheme abc [Switch-isp-abc] quit
# Verify that you can use all read and write commands of the radius and arp features. This example uses radius.
[Switch] radius scheme rad [Switch-radius-rad] primary authentication 2.2.2.2 [Switch-radius-rad] display radius scheme rad … Output of the RADIUS scheme is omitted.
# Verify that you cannot configure any VLAN except VLANs 1 to 20. This example uses VLAN 10 and VLAN 30.
[Switch] vlan 10 [Switch-vlan10] quit [Switch] vlan 30 Permission denied.
# Verify that you cannot configure any interface except Ten-GigabitEthernet 1/0/1 to Ten-GigabitEthernet 1/0/4. This example uses Ten-GigabitEthernet 1/0/2 and Ten-GigabitEthernet 1/0/5.
[Switch] vlan 10 [Switch-vlan10] port ten-gigabitethernet 1/0/2 [Switch-vlan10] port ten-gigabitethernet 1/0/5 Permission denied.