Configuring TC Snooping
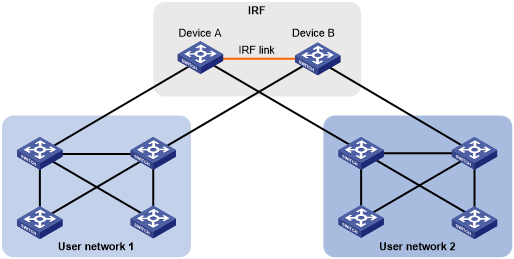
As shown in Figure 30, an IRF fabric connects to two user networks through double links.
Device A and Device B form an IRF fabric.
The spanning tree feature is disabled on Device A and Device B and enabled on all devices in user network 1 and user network 2.
The IRF fabric transparently transmits BPDUs for both user networks and is not involved in the calculation of spanning trees.
When the network topology changes, it takes time for the IRF fabric to update its MAC address table and ARP table. During this period, traffic in the network might be interrupted.
Figure 30: TC Snooping application scenario
To avoid traffic interruption, you can enable TC Snooping on the IRF fabric. After receiving a TC-BPDU through a port, the IRF fabric updates MAC address table and ARP table entries associated with the port's VLAN. In this way, TC Snooping prevents topology change from interrupting traffic forwarding in the network. For more information about the MAC address table and the ARP table, see "Configuring the MAC address table" and Layer 3—IP Services Configuration Guide.