Configuring cross-subnet portal authentication with extended functions
Network requirements
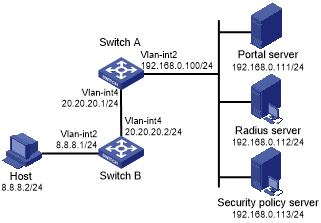
As shown in Figure 55:
Switch A is configured for cross-subnet extended portal authentication. If a user fails security check after passing identity authentication, the user can access only subnet 192.168.0.0/24. After passing security check, the user can access Internet resources.
The host accesses Switch A through Switch B.
A RADIUS server serves as the authentication/accounting server.
Figure 55: Network diagram
Configuration prerequisites and guidelines
Configure IP addresses for the host, switches, and servers as shown in Figure 55 and make sure they can reach each other.
Configure the RADIUS server properly to provide authentication and accounting functions for users.
Make sure the IP address of the portal device added on the portal server is the IP address of the interface connecting users (20.20.20.1 in this example), and the IP address group associated with the portal device is the network segment where the users reside (8.8.8.0/24 in this example).
Configuration procedure
Configure a RADIUS scheme:
# Create a RADIUS scheme named rs1 and enter its view.
<SwitchA> system-view [SwitchA] radius scheme rs1
# Set the server type for the RADIUS scheme. When using the IMC server, set the server type to extended.
[SwitchA-radius-rs1] server-type extended
# Specify the primary authentication server and primary accounting server, and configure the keys for communication with the servers.
[SwitchA-radius-rs1] primary authentication 192.168.0.112 [SwitchA-radius-rs1] primary accounting 192.168.0.112 [SwitchA-radius-rs1] key accounting simple radius [SwitchA-radius-rs1] key authentication simple radius [SwitchA-radius-rs1] user-name-format without-domain
# Configure the IP address of the security policy server.
[SwitchA-radius-rs1] security-policy-server 192.168.0.113 [SwitchA-radius-rs1] quit
Configure an authentication domain:
# Create an ISP domain named dm1 and enter its view.
[SwitchA] domain dm1
# Configure AAA methods for the ISP domain.
[SwitchA-isp-dm1] authentication portal radius-scheme rs1 [SwitchA-isp-dm1] authorization portal radius-scheme rs1 [SwitchA-isp-dm1] accounting portal radius-scheme rs1 [SwitchA-isp-dm1] quit
# Configure domain dm1 as the default ISP domain for all users. Then, if a user enters the username without the ISP domain at logon, the authentication and accounting methods of the default domain are used for the user.
[SwitchA] domain default enable dm1
Configure the ACL (ACL 3000 ) for resources on subnet 192.168.0.0/24 and the ACL (ACL 3001) for Internet resources:
[SwitchA] acl number 3000 [SwitchA-acl-adv-3000] rule permit ip destination 192.168.0.0 0.0.0.255 [SwitchA-acl-adv-3000] rule deny ip [SwitchA-acl-adv-3000] quit [SwitchA] acl number 3001 [SwitchA-acl-adv-3001] rule permit ip [SwitchA-acl-adv-3001] quit
Make sure you specify ACL 3000 as the isolation ACL and ACL 3001 as the security ACL on the security policy server.
Configure portal authentication
# Configure the portal server as follows:
Name: newpt
IP address: 192.168.0.111
Key: portal, in plain text
Port number: 50100
URL: http://192.168.0.111:8080/portal
[SwitchA] portal server newpt ip 192.168.0.111 key simple portal port 50100 url http://192.168.0.111:8080/portal
# Enable portal authentication on the interface connecting Switch B.
[SwitchA] interface vlan-interface 4 [SwitchA–Vlan-interface4] portal server newpt method layer3 [SwitchA–Vlan-interface4] quit
On Switch B, configure a default route to subnet 192.168.0.0/24, setting the next hop as 20.20.20.1. (Details not shown.)