Distributed VXLAN IP gateway deployment
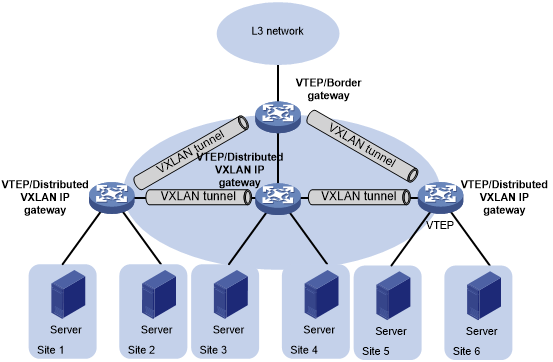
As shown in Figure 15, each site's VTEP acts as a gateway to perform Layer 3 forwarding for the VXLANs of the local site. A VTEP acts as a border gateway to the Layer 3 network for the VXLANs.
Figure 15: Distributed VXLAN IP gateway placement design
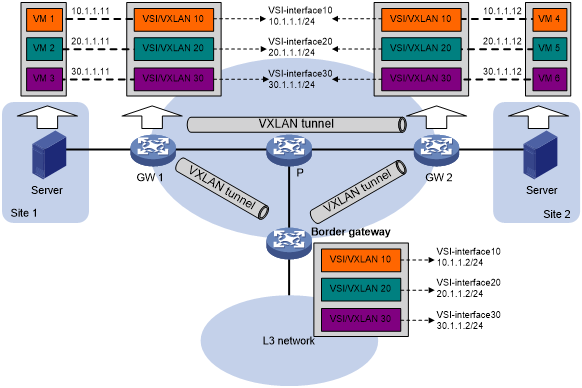
Figure 16 shows an example of distributed VXLAN IP gateway deployment. VSI interfaces are created on each distributed VXLAN IP gateway and the border gateway as gateway interfaces. The same VSI interface uses the same IP address on the distributed VXLAN IP gateways. You must enable one of the following features on a distributed VXLAN IP gateway:
ARP flood suppression. The gateway performs Layer 2 forwarding based on MAC address entries and performs Layer 3 forwarding based on ARP entries.
Local proxy ARP or local ND proxy. The gateway performs Layer 3 forwarding based on ARP or ND entries. The following sections use distributed VXLAN IP gateways enabled with the local proxy ARP or local ND proxy feature to describe the forwarding processes for intra-VXLAN traffic, inter-VXLAN traffic, and traffic from a VXLAN to an external network.
Figure 16: Example of distributed VXLAN IP gateway deployment
Intra-VXLAN traffic forwarding between sites
As shown in Figure 16, the network uses the following process to forward traffic in a VXLAN between sites (for example, from VM 1 to VM 4 in VXLAN 10):
VM 1 sends an ARP request to obtain the MAC address of VM 4.
GW 1 performs the following operations:
Creates an ARP entry for VM 1 and replies with the MAC address of VSI-interface 10 (the gateway interface for VXLAN 10).
Replaces the sender MAC address of the ARP request with the MAC address of VSI-interface 10, and then floods the request to all remote VTEPs.
VM 1 creates an ARP entry for VM 4. The MAC address in the entry is the MAC address of VSI-interface 10 on GW 1.
GW 2 (the VTEP for VM 4) performs the following operations:
De-encapsulates the ARP request and creates an ARP entry for VM 1. The entry contains VM 1's IP address (10.1.1.11), the MAC address of VSI-interface 10 on GW 1, and the incoming tunnel interface.
Replaces the sender MAC address of the request with the MAC address of VSI-interface 10 on GW 2, and then floods the request to the local site in VXLAN 10.
VM 4 creates an ARP entry for VM 1, and then sends a reply to GW 2. The MAC address in the ARP entry is the MAC address of VSI-interface 10 on GW 2.
GW 2 performs the following operations:
Creates an ARP entry for VM 4.
Replaces the sender MAC address of the request with the MAC address of VSI-interface 10 on GW 2, and sends the reply to GW 1.
GW 1 de-encapsulates the ARP request and creates an ARP entry for VM 4. The entry contains VM 4's IP address (10.1.1.12), the MAC address of VSI-interface 10 on GW 2, and the incoming tunnel interface.
For subsequent traffic between VM 1 and VM 4, GW 1 and GW 2 use their respective ARP tables to make the forwarding decision.
Inter-VXLAN traffic forwarding between sites
As shown in Figure 16, the network uses the following process to forward traffic between VXLANs (for example, from VM 1 in VXLAN 10 to VM 5 in VXLAN 20):
VM 1 sends an ARP request to obtain the MAC address of the gateway at 10.1.1.1.
GW 1 creates an ARP entry for VM 1 and replies with the MAC address of VSI-interface 10 (the gateway interface for VXLAN 10).
VM 1 sends the packet destined for VM 5 to GW 1.
GW 1 sends an ARP request to the local site and remote sites to obtain the MAC address of VM 5. In the ARP request, the sender IP address is 20.1.1.1, and the sender MAC address is the MAC address of VSI-interface 20 on GW 1.
GW 2 performs the following operations:
De-encapsulates the ARP request and creates an ARP entry for VM 1. The entry contains VM 1's IP address (20.1.1.1), the MAC address of VSI-interface 20 on GW 1, and the incoming tunnel interface.
Replaces the sender MAC address of the request with the MAC address of VSI-interface 20 on GW 2, and then floods the request to the local site in VXLAN 20.
VM 5 creates an ARP entry for GW 2, and then sends a reply to GW 2. The entry contains the IP address (20.1.1.1) and MAC address of VSI-interface 20 on GW 2).
GW 2 performs the following operations:
Creates an ARP entry for VM 5.
Replaces the sender MAC address in the request with the MAC address of VSI-interface 20 on GW 2, and then sends the reply to GW 1.
GW 1 de-encapsulates the ARP request and creates an ARP entry for VM 5. The entry contains VM 5's IP address 20.1.1.12, the MAC address of VSI-interface 20 on GW 2, and the incoming tunnel interface.
For subsequent traffic between VM 1 and VM 5, GW 1 and GW 2 use their respective ARP tables to make the forwarding decision.
VXLAN-to-external network traffic forwarding
As shown in Figure 16, the network uses the following process to forward traffic from a VXLAN to the Layer 3 network (for example, from VM 1 to the host at 50.1.1.1):
VM 1 sends an ARP request to obtain the MAC address of the gateway at 10.1.1.1.
GW 1 creates an ARP entry for VM 1 and replies with the MAC address of VSI-interface 10 (the gateway interface for VXLAN 10).
VM 1 sends a packet destined for the host to GW 1.
GW 1 performs the following operations:
Searches the IP routing policies or routing table for the next hop. In this example, the next hop for the packet is 10.1.1.2 (the border gateway).
Floods an ARP request to the local and remote sites in VXLAN 10 to obtain the MAC address of 10.1.1.2.
The border gateway de-encapsulates the ARP request, creates an ARP entry for GW 1, and tunnels a reply to GW 1.
GW 1 de-encapsulates the ARP reply and creates an ARP entry for 10.1.1.2.
GW 1 sends the packet destined for the host to the border gateway.
The border gateway de-encapsulates the packet and forwards it to the host.