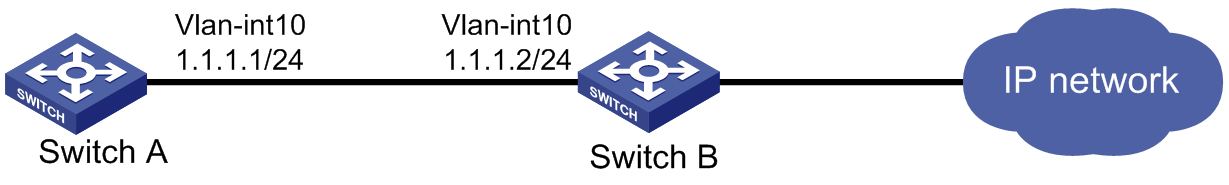
uRPF configuration example
Network requirements
As shown in Figure 131, a client (Switch A) directly connects to an ISP switch (Switch B).
Enable strict uRPF check on Switch A and Switch B to prevent source address spoofing attacks.
Figure 131: Network diagram
Configuration procedure
Enable strict uRPF check on Switch A.
<SwitchA> system-view [SwitchA] ip urpf strict
Enable strict uRPF check on Switch B.
<SwitchB> system-view [SwitchB] ip urpf strict