OSPFv3 IPsec profile configuration example
Network requirements
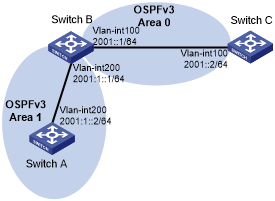
As shown in Figure 112, all switches run OSPFv3, and the AS is divided into two areas.
Configure IPsec profiles on the switches to authenticate and encrypt protocol packets.
Figure 112: Network diagram
Configuration procedure
Configure IPv6 addresses for interfaces. (Details not shown.)
Configure OSPFv3 basic features:
# On Switch A, enable OSPFv3 and specify the router ID as 1.1.1.1.
<SwitchA> system-view [SwitchA] ospfv3 1 [SwitchA-ospfv3-1] router-id 1.1.1.1 [SwitchA-ospfv3-1] quit [SwitchA] interface vlan-interface 200 [SwitchA-Vlan-interface200] ospfv3 1 area 1 [SwitchA-Vlan-interface200] quit
# On Switch B, enable OSPFv3 and specify the router ID as 2.2.2.2.
<SwitchB> system-view [SwitchB] ospfv3 1 [SwitchB-ospfv3-1] router-id 2.2.2.2 [SwitchB-ospfv3-1] quit [SwitchB] interface vlan-interface 100 [SwitchB-Vlan-interface100] ospfv3 1 area 0 [SwitchB-Vlan-interface100] quit [SwitchB] interface vlan-interface 200 [SwitchB-Vlan-interface200] ospfv3 1 area 1 [SwitchB-Vlan-interface200] quit
# On Switch C, enable OSPFv3 and specify the router ID as 3.3.3.3.
<SwitchC> system-view [SwitchC] ospfv3 1 [SwitchC-ospfv3-1] router-id 3.3.3.3 [SwitchC-ospfv3-1] quit [SwitchC] interface vlan-interface 100 [SwitchC-Vlan-interface100] ospfv3 1 area 0 [SwitchC-Vlan-interface100] quit
Configure OSPFv3 IPsec profiles:
On Switch A:
# Create an IPsec transform set named trans.
[SwitchA] ipsec transform-set trans
# Specify the encapsulation mode as transport.
[SwitchA-ipsec-transform-set-trans] encapsulation-mode transport
# Specify the ESP encryption and authentication algorithms.
[SwitchA-ipsec-transform-set-trans] esp encryption-algorithm 3des-cbc [SwitchA-ipsec-transform-set-trans] esp authentication-algorithm md5
# Specify the AH authentication algorithm.
[SwitchA-ipsec-transform-set-trans] ah authentication-algorithm md5 [SwitchA-ipsec-transform-set-trans] quit
# Create a manual IPsec profile named profile001.
[SwitchA] ipsec profile profile001 manual
# Use IPsec transform set trans.
[SwitchA-ipsec-profile-profile001-manual] transform-set trans
# Configure the inbound and outbound SPIs for AH.
[SwitchA-ipsec-profile-profile001-manual] sa spi inbound ah 111111111 [SwitchA-ipsec-profile-profile001-manual] sa spi outbound ah 111111111
# Configure the inbound and outbound SPIs for ESP.
[SwitchA-ipsec-profile-profile001-manual] sa spi inbound esp 200000 [SwitchA-ipsec-profile-profile001-manual] sa spi outbound esp 200000
# Configure the inbound and outbound SA keys for AH.
[SwitchA-ipsec-profile-profile001-manual] sa string-key inbound ah simple abc [SwitchA-ipsec-profile-profile001-manual] sa string-key outbound ah simple abc
# Configure the inbound and outbound SA keys for ESP.
[SwitchA-ipsec-profile-profile001-manual] sa string-key inbound esp simple 123 [SwitchA-ipsec-profile-profile001-manual] sa string-key outbound esp simple 123 [SwitchA-ipsec-profile-profile001-manual] quit
On Switch B:
# Create an IPsec transform set named trans.
[SwitchB] ipsec transform-set trans
# Specify the encapsulation mode as transport.
[SwitchB-ipsec-transform-set-trans] encapsulation-mode transport
# Specify the ESP encryption and authentication algorithms.
[SwitchB-ipsec-transform-set-trans] esp encryption-algorithm 3des-cbc [SwitchB-ipsec-transform-set-trans] esp authentication-algorithm md5
# Specify the AH authentication algorithm.
[SwitchB-ipsec-transform-set-trans] ah authentication-algorithm md5 [SwitchB-ipsec-transform-set-trans] quit
# Create a manual IPsec profile named profile001.
[SwitchB] ipsec profile profile001 manual
# Use IPsec transform set trans.
[SwitchB-ipsec-profile-profile001-manual] transform-set trans
# Configure the inbound and outbound SPIs for AH.
[SwitchB-ipsec-profile-profile001-manual] sa spi inbound ah 111111111 [SwitchB-ipsec-profile-profile001-manual] sa spi outbound ah 111111111
# Configure the inbound and outbound SPIs for ESP.
[SwitchB-ipsec-profile-profile001-manual] sa spi inbound esp 200000 [SwitchB-ipsec-profile-profile001-manual] sa spi outbound esp 200000
# Configure the inbound and outbound SA keys for AH.
[SwitchB-ipsec-profile-profile001-manual] sa string-key inbound ah simple abc [SwitchB-ipsec-profile-profile001-manual] sa string-key outbound ah simple abc
# Configure the inbound and outbound SA keys for ESP.
[SwitchB-ipsec-profile-profile001-manual] sa string-key inbound esp simple 123 [SwitchB-ipsec-profile-profile001-manual] sa string-key outbound esp simple 123 [SwitchB-ipsec-profile-profile001-manual] quit
# Create a manual IPsec profile named profile002.
[SwitchB] ipsec profile profile002 manual
# Use IPsec transform set trans.
[SwitchB-ipsec-profile-profile002-manual] transform-set trans
# Configure the inbound and outbound SPIs for AH.
[SwitchB-ipsec-profile-profile002-manual] sa spi inbound ah 4294967295 [SwitchB-ipsec-profile-profile002-manual] sa spi outbound ah 4294967295
# Configure the inbound and outbound SPIs for ESP.
[SwitchB-ipsec-profile-profile002-manual] sa spi inbound esp 256 [SwitchB-ipsec-profile-profile002-manual] sa spi outbound esp 256
# Configure the inbound and outbound SA keys for AH.
[SwitchB-ipsec-profile-profile002-manual] sa string-key inbound ah simple hello [SwitchB-ipsec-profile-profile002-manual] sa string-key outbound ah simple hello
# Configure the inbound and outbound SA keys for ESP.
[SwitchB-ipsec-profile-profile002-manual] sa string-key inbound esp simple byebye [SwitchB-ipsec-profile-profile002-manual] sa string-key outbound esp simple byebye [SwitchB-ipsec-profile-profile002-manual] quit
On Switch C:
# Create an IPsec transform set named trans.
[SwitchC] ipsec transform-set trans
# Specify the encapsulation mode as transport.
[SwitchC-ipsec-transform-set-trans] encapsulation-mode transport
# Specify the ESP encryption and authentication algorithms.
[SwitchC-ipsec-transform-set-trans] esp encryption-algorithm 3des-cbc [SwitchC-ipsec-transform-set-trans] esp authentication-algorithm md5
# Specify the AH authentication algorithm.
[SwitchC-ipsec-transform-set-trans] ah authentication-algorithm md5 [SwitchC-ipsec-transform-set-trans] quit
# Create a manual IPsec profile named profile002.
[SwitchC] ipsec profile profile002 manual
# Use IPsec transform set trans.
[SwitchC-ipsec-profile-profile002-manual] transform-set trans
# Configure the inbound and outbound SPIs for AH.
[SwitchC-ipsec-profile-profile002-manual] sa spi inbound ah 4294967295 [SwitchC-ipsec-profile-profile002-manual] sa spi outbound ah 4294967295
# Configure the inbound and outbound SPIs for ESP.
[SwitchC-ipsec-profile-profile002-manual] sa spi inbound esp 256 [SwitchC-ipsec-profile-profile002-manual] sa spi outbound esp 256
# Configure the inbound and outbound SA keys for AH.
[SwitchC-ipsec-profile-profile002-manual] sa string-key inbound ah simple hello [SwitchC-ipsec-profile-profile002-manual] sa string-key outbound ah simple hello
# Configure the inbound and outbound SA keys for ESP.
[SwitchC-ipsec-profile-profile002-manual] sa string-key inbound esp simple byebye [SwitchC-ipsec-profile-profile002-manual] sa string-key outbound esp simple byebye [SwitchC-ipsec-profile-profile002-manual] quit
Apply the IPsec profiles to areas:
# Configure Switch A.
[SwitchA] ospfv3 1 [SwitchA-ospfv3-1] area 1 [SwitchA-ospfv3-1-area-0.0.0.1] enable ipsec-profile profile001 [SwitchA-ospfv3-1-area-0.0.0.1] quit [SwitchA-ospfv3-1] quit
# Configure Switch B.
[SwitchB] ospfv3 1 [SwitchB-ospfv3-1] area 0 [SwitchB-ospfv3-1-area-0.0.0.0] enable ipsec-profile profile002 [SwitchB-ospfv3-1-area-0.0.0.0] quit [SwitchB-ospfv3-1] area 1 [SwitchB-ospfv3-1-area-0.0.0.1] enable ipsec-profile profile001 [SwitchB-ospfv3-1-area-0.0.0.1] quit [SwitchB-ospfv3-1] quit
# Configure Switch C.
[SwitchC] ospfv3 1 [SwitchC-ospfv3-1] area 0 [SwitchC-ospfv3-1-area-0.0.0.0] enable ipsec-profile profile002 [SwitchC-ospfv3-1-area-0.0.0.0] quit [SwitchC-ospfv3-1] quit
Verifying the configuration
# Verify that OSPFv3 packets between Switches A, B, and C are protected by IPsec. (Details not shown.)