EVPN-based service chain PBR configuration example
Network requirements
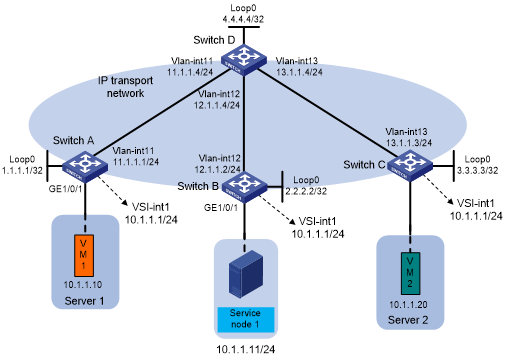
As shown in Figure 91, Switch A, Switch B, and Switch C are distributed EVPN gateway devices. Switch D acts as a route reflector to reflect BGP routes for the other switches.
Configure PBR to direct packets sent by Server 1 to Service node 1. After being processed, the packets are forwarded to Server 2.
Figure 91: Network diagram
Configuration procedure
Configure IP addresses and subnet masks for interfaces, as shown in Figure 91. (Details not shown.)
Configure Switch A:
# Enable L2VPN.
<SwitchA> system-view [SwitchA] l2vpn enable
# Disable remote-MAC address learning and remote ARP learning.
[SwitchA] vxlan tunnel mac-learning disable [SwitchA] vxlan tunnel arp-learning disable
# Create an EVPN instance in VSI instance view, and configure the system to automatically generate an RT and RD.
[SwitchA] vsi vpna [SwitchA-vsi-vpna] evpn encapsulation vxlan [SwitchA-vsi-vpna-evpn-vxlan] route-distinguisher auto [SwitchA-vsi-vpna-evpn-vxlan] vpn-target auto [SwitchA-vsi-vpna-evpn-vxlan] quit
# Create VXLAN 10.
[SwitchA-vsi-vpna] vxlan 10 [SwitchA-vsi-vpna-vxlan-10] quit [SwitchA-vsi-vpna] quit
# Configure BGP to advertise EVPN routes.
[SwitchA] bgp 200 [SwitchA-bgp-default] peer 4.4.4.4 as-number 200 [SwitchA-bgp-default] peer 4.4.4.4 connect-interface loopback 0 [SwitchA-bgp-default] address-family l2vpn evpn [SwitchA-bgp-default-evpn] peer 4.4.4.4 enable [SwitchA-bgp-default-evpn] quit [SwitchA-bgp-default] quit
# Create VPN instance vpna.
[SwitchA] ip vpn-instance vpna [SwitchA-vpn-instance-vpna] route-distinguisher 1:1 [SwitchA-vpn-instance-vpna] address-family ipv4 [SwitchA-vpn-ipv4-vpna] vpn-target 2:2 [SwitchA-vpn-ipv4-vpna] quit [SwitchA-vpn-instance-vpna] address-family evpn [SwitchA-vpn-evpn-vpna] vpn-target 1:1
# Configure VSI-interface 1.
[SwitchA] interface vsi-interface 1 [SwitchA-Vsi-interface1] ip binding vpn-instance vpna [SwitchA-Vsi-interface1] ip address 10.1.1.1 255.255.255.0 [SwitchA-Vsi-interface1] mac-address 0001-0001-0001 [SwitchA-Vsi-interface1] local-proxy-arp enable [SwitchA-Vsi-interface1] distributed-gateway local [SwitchA-Vsi-interface1] quit
# Configure VSI-interface 3, associate the interface with VPN instance vpna, and set the L3 VXLAN ID to 1000.
[SwitchA] interface vsi-interface 3 [SwitchA-Vsi-interface3] ip binding vpn-instance vpna [SwitchA-Vsi-interface3] l3-vni 1000 [SwitchA-Vsi-interface3] quit
# Associate VSI instance vpna with VSI-interface 1.
[SwitchA] vsi vpna [SwitchA-vsi-vpna] gateway vsi-interface 1 [SwitchA-vsi-vpna] quit
# Configure VLAN-interface 11.
[SwitchA] interface vlan-interface 11 [SwitchA-Vlan-interface11] ip address 11.1.1.1 255.255.255.0 [SwitchA-Vlan-interface11] ospf 1 area 0.0.0.0 [SwitchA-Vlan-interface11] quit
# Associate Ethernet service instance 1000 with VSI instance vpna.
[SwitchA] interface gigabitethernet 1/0/1 [SwitchA-GigabitEthernet1/0/1] port link-mode bridge [SwitchA-GigabitEthernet1/0/1] service-instance 1000 [SwitchA-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 2 [SwitchA-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
# Create ACL 3000 to permit packets with source IP address 10.1.1.10 and destination IP address 10.1.1.20.
<SwitchA> system-view [SwitchA] acl advanced 3000 [SwitchA-acl-ipv4-adv-3000] rule 0 permit ip source 10.1.1.10 0 destination 10.1.1.20 0
# Create node 0, use ACL 3000 to match packets with source IP address 10.1.1.1 and destination IP address 10.1.1.20. Apply next hop 10.1.1.11 and service chain path ID 1 to matching packets.
[SwitchA] policy-based-route aa permit node 0 [SwitchA-pbr-aa-0] if-match acl 3000 [SwitchA-pbr-aa-0] apply service-chain path-id 1 [SwitchA-pbr-aa-0] apply next-hop vpn-instance vpna 10.1.1.11
# Apply policy aa to VSI-interface 3.
[SwitchA] interface vsi-interface 1 [SwitchA-Vsi-interface1] ip policy-based-route aa [SwitchA-Vsi-interface1] quit
Configure Switch B:
# Enable L2VPN.
<SwitchB> system-view [SwitchB] l2vpn enable
# Disable remote-MAC address learning and remote ARP learning.
[SwitchB] vxlan tunnel mac-learning disable [SwitchB] vxlan tunnel arp-learning disable
# Create an EVPN instance in VSI instance view, and configure the system to automatically generate an RT and RD.
[SwitchB] vsi vpna [SwitchB-vsi-vpna] evpn encapsulation vxlan [SwitchB-vsi-vpna-evpn-vxlan] route-distinguisher auto [SwitchB-vsi-vpna-evpn-vxlan] vpn-target auto [SwitchB-vsi-vpna-evpn-vxlan] quit
# Configure VXLAN 10.
[SwitchB-vsi-vpna] vxlan 10 [SwitchB-vsi-vpna-vxlan-10] quit [SwitchB-vsi-vpna] quit
# Configure BGP to advertise EVPN routes.
[SwitchB] bgp 200 [SwitchB-bgp-default] peer 4.4.4.4 as-number 200 [SwitchB-bgp-default] peer 4.4.4.4 connect-interface loopback0 [SwitchB-bgp-default] address-family l2vpn evpn [SwitchB-bgp-default-evpn] peer 4.4.4.4 enable
# Create VPN instance vpna.
[SwitchB] ip vpn-instance vpna [SwitchB-vpn-instance-vpna] route-distinguisher 1:1 [SwitchB-vpn-instance-vpna] address-family ipv4 [SwitchB-vpn-ipv4-vpna] vpn-target 2:2 [SwitchB-vpn-ipv4-vpna] quit [SwitchB-vpn-instance-vpna] address-family evpn [SwitchB-vpn-evpn-vpna] vpn-target 1:1 [SwitchB-vpn-evpn-vpna] quit
# Configure VSI-interface 1.
[SwitchB] interface vsi-interface 1 [SwitchB-Vsi-interface1] ip binding vpn-instance vpna [SwitchB-Vsi-interface1] ip address 10.1.1.1 255.255.255.0 [SwitchB-Vsi-interface1] mac-address 0001-0001-0001 [SwitchB-Vsi-interface1] local-proxy-arp enable [SwitchB-Vsi-interface1] distributed-gateway local [SwitchB-Vsi-interface1] quit
# Associate VSI instance vpna with VSI-interface 1.
[SwitchB] vsi vpna [SwitchB-vsi-vpna] gateway vsi-interface 1 [SwitchB-vsi-vpna] quit
# Configure VSI-interface 3.
[SwitchB] interface vsi-interface 3 [SwitchB-Vsi-interface3] ip binding vpn-instance vpna [SwitchB-Vsi-interface3] l3-vni 1000 [SwitchB-Vsi-interface3] quit
# Configure GigabitEthernet 1/0/1 as an AC interface.
[SwitchB] interface gigabitethernet 1/0/1 [SwitchB-GigabitEthernet1/0/1] port link-mode bridge [SwitchB-GigabitEthernet1/0/1] service-instance 1000 [SwitchB-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 2 [SwitchB-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna [SwitchB-GigabitEthernet1/0/1-srv1000] quit [SwitchB-GigabitEthernet1/0/1] quit
# Create node 0 and apply next hop 10.1.1.11 to packets with service chain path ID 1.
[SwitchB] policy-based-route aa permit node 0 [SwitchB-pbr-aa-0] if-match service-chain path-id 1 [SwitchB-pbr-aa-0] apply next-hop vpn-instance vpna 10.1.1.11 [SwitchB-pbr-aa-0] quit
# Apply policy aa to VSI-interface 3.
[SwitchB] interface vsi-interface 3 [SwitchB-Vsi-interface3] ip policy-based-route aa [SwitchB-Vsi-interface3] quit
Configure Switch C:
# Enable L2VPN.
<SwitchC> system-view [SwitchC] l2vpn enable
# Disable remote-MAC address learning and remote ARP learning.
[SwitchC] vxlan tunnel mac-learning disable [SwitchC] vxlan tunnel arp-learning disable
# Create an EVPN instance in VSI instance view, and configure the system to automatically generate an RT and RD.
[SwitchC] vsi vpna [SwitchC-vsi-vpna] evpn encapsulation vxlan [SwitchC-vsi-vpna-evpn-vxlan] route-distinguisher auto [SwitchC-vsi-vpna-evpn-vxlan] vpn-target auto [SwitchC-vsi-vpna-evpn-vxlan] quit
# Configure VXLAN 10.
[SwitchC-vsi-vpna] vxlan 10 [SwitchC-vsi-vpna-vxlan-10] quit [SwitchC-vsi-vpna] quit
# Configure BGP to advertise EVPN routes.
[SwitchC] bgp 200 [SwitchC-bgp-default] peer 4.4.4.4 as-number 200 [SwitchC-bgp-default] peer 4.4.4.4 connect-interface loopback 0 [SwitchC-bgp-default] address-family l2vpn evpn [SwitchC-bgp-default-evpn] peer 4.4.4.4 enable [SwitchC-bgp-default-evpn] quit [SwitchC-bgp-default] quit
# Create VPN instance vpna.
[SwitchC] ip vpn-instance vpna [SwitchC-vpn-instance-vpna] route-distinguisher 1:1 [SwitchC-vpn-instance-vpna] address-family ipv4 [SwitchC-vpn-ipv4-vpna] vpn-target 2:2 [SwitchC-vpn-ipv4-vpna] quit [SwitchC-vpn-instance-vpna] address-family evpn [SwitchC-vpn-evpn-vpna] vpn-target 1:1 [SwitchC-vpn-evpn-vpna] quit
# Create VSI-interface 1, assign an IP address to it, and specify the interface as a distributed gateway in VXLAN 10.
[SwitchC] interface vsi-interface 1 [SwitchC-Vsi-interface1] ip binding vpn-instance vpna [SwitchC-Vsi-interface1] ip address 10.1.1.1 255.255.255.0 [SwitchC-Vsi-interface1] mac-address 0001-0001-0001 [SwitchC-Vsi-interface1] local-proxy-arp enable [SwitchC-Vsi-interface1] distributed-gateway local [SwitchC-Vsi-interface1] quit
# Associate VSI instance vpna with VSI-interface 1.
[SwitchC] vsi vpna [SwitchC-vsi-vpna] gateway vsi-interface 1 [SwitchC-vsi-vpna] quit
# Bind VSI instance vpna to GigabitEthernet 1/0/1.
[SwitchC] interface gigabitethernet 1/0/1 [SwitchC-GigabitEthernet1/0/1] port link-mode bridge [SwitchC-GigabitEthernet1/0/1] service-instance 2000 [SwitchC-GigabitEthernet1/0/1-srv2000] encapsulation s-vid 2 [SwitchC-GigabitEthernet1/0/1] xconnect vsi vpna [SwitchC-GigabitEthernet1/0/1] quit
Configure Switch D:
# Configure Switch D to establish BGP connections with the other switches.
<SwitchD> system-view [SwitchD] bgp 200 [SwitchD-bgp-default] group evpn [SwitchD-bgp-default] peer 1.1.1.1 group evpn [SwitchD-bgp-default] peer 2.2.2.2 group evpn [SwitchD-bgp-default] peer 3.3.3.3 group evpn [SwitchD-bgp-default] peer evpn as-number 200 [SwitchD-bgp-default] peer evpn connect-interface loopback 0
# Configure BGP to advertise EVPN routes, and disable route target filtering for BGP EVPN routes.
[SwitchD-bgp-default] address-family l2vpn evpn [SwitchD-bgp-default-evpn] peer evpn enable [SwitchD-bgp-default-evpn] undo policy vpn-target
# Configure Switch D as a route reflector.
[SwitchD-bgp-default-evpn] peer evpn reflect-client [SwitchD-bgp-default-evpn] quit [SwitchD-bgp-default] quit
# Configure VLAN-interface 11.
[SwitchD] interface vlan-interface 11 [SwitchD-Vlan-interface11] ip address 11.1.1.4 255.255.255.0 [SwitchD-Vlan-interface11] ospf 1 area 0.0.0.0 [SwitchD-Vlan-interface11] quit
# Configure VLAN-interface 12.
[SwitchD] interface vlan-interface 12 [SwitchD-Vlan-interface12] ip address 12.1.1.4 255.255.255.0 [SwitchD-Vlan-interface12] ospf 1 area 0.0.0.0 [SwitchD-Vlan-interface12] quit
# Configure VLAN-interface 13.
[SwitchD] interface Vlan-interface 13 [SwitchD-Vlan-interface13] ip address 13.1.1.4 255.255.255.0 [SwitchD-Vlan-interface13] ospf 1 area 0.0.0.0 [SwitchD-Vlan-interface13] quit
Verifying the configuration
# Capture packets sent from Server 1 to Server 2 in Ethernet service instance 1000. (Details not shown.)
The packets are processed by Service node 1 before they are delivered to Server 2.