IPsec for IPv6 BGP packets configuration example
Network requirements
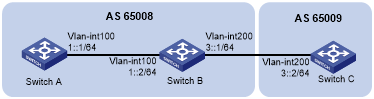
As shown in Figure 86, all switches run IPv6 BGP. Establish an IBGP connection between Switch A and Switch B, and establish an EBGP connection between Switch B and Switch C.
To enhance security, configure IPsec to protect IPv6 BGP packets.
Figure 86: Network diagram
Configuration procedure
Configure IPv6 addresses for interfaces. (Details not shown.)
Establish an IBGP connection between Switch A and Switch B:
# Configure Switch A.
<SwitchA> system-view [SwitchA] bgp 65008 [SwitchA-bgp-default] router-id 1.1.1.1 [SwitchA-bgp-default] group ibgp internal [SwitchA-bgp-default] peer 1::2 group ibgp [SwitchA-bgp-default] address-family ipv6 unicast [SwitchA-bgp-default-ipv6] peer ibgp enable [SwitchA-bgp-default-ipv6] quit [SwitchA-bgp-default] quit
# Configure Switch B.
<SwitchB> system-view [SwitchB] bgp 65008 [SwitchB-bgp-default] router-id 2.2.2.2 [SwitchB-bgp-default] group ibgp internal [SwitchB-bgp-default] peer 1::1 group ibgp [SwitchB-bgp-default] address-family ipv6 unicast [SwitchB-bgp-default-ipv6] peer ibgp enable [SwitchB-bgp-default-ipv6] quit
Establish an EBGP connection between Switch B and Switch C:
# Configure Switch C.
<SwitchC> system-view [SwitchC] bgp 65009 [SwitchC-bgp-default] router-id 3.3.3.3 [SwitchC-bgp-default] group ebgp external [SwitchC-bgp-default] peer 3::1 as-number 65008 [SwitchC-bgp-default] peer 3::1 group ebgp [SwitchC-bgp-default] address-family ipv6 unicast [SwitchC-bgp-default-ipv6] peer ebgp enable [SwitchC-bgp-default-ipv6] quit [SwitchC-bgp-default] quit
# Configure Switch B.
[SwitchB-bgp-default] group ebgp external [SwitchB-bgp-default] peer 3::2 as-number 65009 [SwitchB-bgp-default] peer 3::2 group ebgp [SwitchB-bgp-default] address-family ipv6 unicast [SwitchB-bgp-default-ipv6] peer ebgp enable [SwitchB-bgp-default-ipv6] quit [SwitchB-bgp-default] quit
Configure IPsec transform sets and IPsec profiles:
# On Switch A, create an IPsec transform set named tran1.
[SwitchA] ipsec transform-set tran1
# Set the encapsulation mode to transport mode.
[SwitchA-ipsec-transform-set-tran1] encapsulation-mode transport
# Set the security protocol to ESP, the encryption algorithm to DES, and authentication algorithm to SHA1.
[SwitchA-ipsec-transform-set-tran1] esp encryption-algorithm des [SwitchA-ipsec-transform-set-tran1] esp authentication-algorithm sha1 [SwitchA-ipsec-transform-set-tran1] quit
# Create an IPsec profile named policy001, and specify the manual mode for it.
[SwitchA] ipsec profile policy001 manual
# Use IPsec transform set tran1.
[SwitchA-ipsec-profile-policy001-manual] transform-set tran1
# Set the SPIs of the inbound and outbound SAs to 12345.
[SwitchA-ipsec-profile-policy001-manual] sa spi outbound esp 12345 [SwitchA-ipsec-profile-policy001-manual] sa spi inbound esp 12345
# Set the keys for the inbound and outbound SAs using ESP to abcdefg.
[SwitchA-ipsec-profile-policy001-manual] sa string-key outbound esp simple abcdefg [SwitchA-ipsec-profile-policy001-manual] sa string-key inbound esp simple abcdefg [SwitchA-ipsec-profile-policy001-manual] quit
# On Switch B, create an IPsec transform set named tran1.
[SwitchB] ipsec transform-set tran1
# Set the encapsulation mode to transport mode.
[SwitchB-ipsec-transform-set-tran1] encapsulation-mode transport
# Set the security protocol to ESP, the encryption algorithm to DES, and authentication algorithm to SHA1.
[SwitchB-ipsec-transform-set-tran1] esp encryption-algorithm des [SwitchB-ipsec-transform-set-tran1] esp authentication-algorithm sha1 [SwitchB-ipsec-transform-set-tran1] quit
# Create IPsec profile named policy001, and specify the manual mode for it.
[SwitchB] ipsec profile policy001 manual
# Use IPsec transform set tran1.
[SwitchB-ipsec-profile-policy001-manual] transform-set tran1
# Set the SPIs of the inbound and outbound SAs to 12345.
[SwitchB-ipsec-profile-policy001-manual] sa spi outbound esp 12345 [SwitchB-ipsec-profile-policy001-manual] sa spi inbound esp 12345
# Set the keys for the inbound and outbound SAs using ESP to abcdefg.
[SwitchB-ipsec-profile-policy001-manual] sa string-key outbound esp simple abcdefg [SwitchB-ipsec-profile-policy001-manual] sa string-key inbound esp simple abcdefg [SwitchB-ipsec-profile-policy001-manual] quit
# Create an IPsec transform set named tran2.
[SwitchB] ipsec transform-set tran2
# Set the encapsulation mode to transport mode.
[SwitchB-ipsec-transform-set-tran2] encapsulation-mode transport
# Set the security protocol to ESP, the encryption algorithm to DES, and authentication algorithm to SHA1.
[SwitchB-ipsec-transform-set-tran2] esp encryption-algorithm des [SwitchB-ipsec-transform-set-tran2] esp authentication-algorithm sha1 [SwitchB-ipsec-transform-set-tran2] quit
# Create IPsec profile named policy002, and specify the manual mode for it.
[SwitchB] ipsec profile policy002 manual
# Use IPsec transform set tran2.
[SwitchB-ipsec-profile-policy002-manual] transform-set tran2
# Set the SPIs of the inbound and outbound SAs to 54321.
[SwitchB-ipsec-profile-policy002-manual] sa spi outbound esp 54321 [SwitchB-ipsec-profile-policy002-manual] sa spi inbound esp 54321
# Set the keys for the inbound and outbound SAs using ESP to gfedcba.
[SwitchB-ipsec-profile-policy002-manual] sa string-key outbound esp simple gfedcba [SwitchB-ipsec-profile-policy002-manual] sa string-key inbound esp simple gfedcba [SwitchB-ipsec-profile-policy002-manual] quit
# On Switch C, create an IPsec transform set named tran2.
[SwitchC] ipsec transform-set tran2
# Set the encapsulation mode to transport mode.
[SwitchC-ipsec-transform-set-tran2] encapsulation-mode transport
# Set the security protocol to ESP, the encryption algorithm to DES, and authentication algorithm to SHA1.
[SwitchC-ipsec-transform-set-tran2] esp encryption-algorithm des [SwitchC-ipsec-transform-set-tran2] esp authentication-algorithm sha1 [SwitchC-ipsec-transform-set-tran2] quit
# Create IPsec profile named policy002, and specify the manual mode for it.
[SwitchC] ipsec profile policy002 manual
# Use IPsec transform set tran2.
[SwitchC-ipsec-profile-policy002-manual] transform-set tran2
# Set the SPIs of the inbound and outbound SAs to 54321.
[SwitchC-ipsec-profile-policy002-manual] sa spi outbound esp 54321 [SwitchC-ipsec-profile-policy002-manual] sa spi inbound esp 54321
# Set the keys for the inbound and outbound SAs using ESP to gfedcba.
[SwitchC-ipsec-profile-policy002-manual] sa string-key outbound esp simple gfedcba [SwitchC-ipsec-profile-policy002-manual] sa string-key inbound esp simple gfedcba [SwitchC-ipsec-profile-policy002-manual] quit
Configure IPsec to protect IPv6 BGP packets between Switch A and Switch B:
# Configure Switch A.
[SwitchA] bgp 65008 [SwitchA-bgp-default] peer 1::2 ipsec-profile policy001 [SwitchA-bgp-default] quit
# Configure Switch B.
[SwitchB] bgp 65008 [SwitchB-bgp-default] peer 1::1 ipsec-profile policy001 [SwitchB-bgp-default] quit
Configure IPsec to protect IPv6 BGP packets between Router B and Switch C:
# Configure Switch C.
[SwitchC] bgp 65009 [SwitchC-bgp-default] peer ebgp ipsec-profile policy002 [SwitchC-bgp-default] quit
# Configure Switch B.
[SwitchB] bgp 65008 [SwitchB-bgp-default] peer ebgp ipsec-profile policy002 [SwitchB-bgp-default] quit
Verifying the configuration
# Display detailed information about IPv6 BGP peers on Switch B.
[SwitchB] display bgp peer ipv6 verbose
Peer: 1::1 Local: 2.2.2.2
Type: IBGP link
BGP version 4, remote router ID 1.1.1.1
BGP current state: Established, Up for 00h05m54s
BGP current event: KATimerExpired
BGP last state: OpenConfirm
Port: Local - 24896 Remote - 179
Configured: Active Hold Time: 180 sec Keepalive Time: 60 sec
Received : Active Hold Time: 180 sec
Negotiated: Active Hold Time: 180 sec Keepalive Time: 60 sec
Peer optional capabilities:
Peer support BGP multi-protocol extended
Peer support BGP route refresh capability
Peer support BGP route AS4 capability
Address family IPv6 Unicast: advertised and received
InQ updates: 0, OutQ updates: 0
NLRI statistics:
Rcvd: UnReach NLRI 0, Reach NLRI 0
Sent: UnReach NLRI 0, Reach NLRI 3
Message statistics:
Msg type Last rcvd time/ Current rcvd count/ History rcvd count/
Last sent time Current sent count History sent count
Open 18:59:15-2013.4.24 1 1
18:59:15-2013.4.24 1 2
Update - 0 0
18:59:16-2013.4.24 1 1
Notification - 0 0
18:59:15-2013.4.24 0 1
Keepalive 18:59:15-2013.4.24 1 1
18:59:15-2013.4.24 1 1
RouteRefresh - 0 0
- 0 0
Total - 2 2
- 3 5
Maximum allowed prefix number: 4294967295
Threshold: 75%
Minimum time between advertisements is 15 seconds
Optional capabilities:
Multi-protocol extended capability has been enabled
Route refresh capability has been enabled
Peer preferred value: 0
IPsec profile name: policy001
Routing policy configured:
No routing policy is configured
Peer: 3::2 Local: 2.2.2.2
Type: EBGP link
BGP version 4, remote router ID 3.3.3.3
BGP current state: Established, Up for 00h05m00s
BGP current event: KATimerExpired
BGP last state: OpenConfirm
Port: Local - 24897 Remote - 179
Configured: Active Hold Time: 180 sec Keepalive Time: 60 sec
Received : Active Hold Time: 180 sec
Negotiated: Active Hold Time: 180 sec Keepalive Time: 60 sec
Peer optional capabilities:
Peer support BGP multi-protocol extended
Peer support BGP route refresh capability
Peer support BGP route AS4 capability
Address family IPv6 Unicast: advertised and received
Received: Total 8 messages, Update messages 1
Sent: Total 8 messages, Update messages 1
Maximum allowed prefix number: 4294967295
Threshold: 75%
Minimum time between advertisements is 30 seconds
Optional capabilities:
Multi-protocol extended capability has been enabled
Route refresh capability has been enabled
Peer preferred value: 0
IPsec profile name: policy002
Routing policy configured:
No routing policy is configured