L2TP features
Flexible identity authentication mechanism and high security—L2TP by itself does not provide security for connections. However, it has all the security features of PPP and allows for PPP authentication (CHAP or PAP). L2TP can also cooperate with IPsec to improve security for tunneled data.
Multiprotocol transmission—L2TP tunnels PPP frames, which can be used to encapsulate packets of multiple network layer protocols.
RADIUS authentication—An LAC or LNS can send the username and password of a remote user to a RADIUS server for authentication.
Private address allocation—An LNS can dynamically allocate private addresses to remote users. This facilitates address allocation for private internets (RFC 1918) and improves security.
Flexible accounting—Accounting can be simultaneously performed on the LAC and LNS. This allows bills to be generated on the ISP side and charging and auditing to be processed on the enterprise gateway. L2TP can provide accounting data, including inbound and outbound traffic statistics (in packets and bytes) and the connection's start time and end time. The AAA server uses these data for flexible accounting.
Reliability—L2TP supports LNS backup. When the connection to the primary LNS is torn down, an LAC can establish a new connection to a secondary LNS. This redundancy enhances the reliability of L2TP services.
Issuing tunnel attributes by RADIUS server to LAC—In NAS-initiated mode, the tunnel attributes can be issued by the RADIUS server to the LAC. For the LAC to receive these attributes, enable L2TP and configure remote AAA authentication for PPP users on the LAC.
When an L2TP user dials in to the LAC, the LAC as the RADIUS client sends the user information to the RADIUS server. The RADIUS server authenticates the PPP user, returns the result to the LAC, and issues L2TP tunnel attributes for the PPP user to the LAC. The LAC then sets up an L2TP tunnel and sessions based on the issued L2TP tunnel attributes.
Table 2: Tunnel attributes that can be issued by the RADIUS server
Attribute number | Attribute name | Description |
|---|---|---|
64 | Tunnel-Type | Tunnel type, which can only be L2TP. |
65 | Tunnel-Medium-Type | Transmission medium type for the tunnel, which can only be IPv4. |
67 | Tunnel-Server-Endpoint | IP address of the LNS. |
69 | Tunnel-Password | Key used to authenticate a peer of the tunnel. |
81 | Tunnel-Private-Group-ID | Group ID for the tunnel. The LAC sends this value to the LNS for the LNS to perform an operation accordingly. |
82 | Tunnel-Assignment-ID | Assignment ID for the tunnel. It is used to indicate the tunnel to which a session is assigned. L2TP users with the same Tunnel-Assignment-ID, Tunnel-Server-Endpoint, and Tunnel-Password attributes share an L2TP tunnel. |
90 | Tunnel-Client-Auth-ID | Tunnel name. It is used to indicate the local tunnel. |
The RADIUS server can issue only one set of the L2TP tunnel attributes in a RADIUS packet.
The RADIUS-issued tunnel attributes override the tunnel attributes manually configured on the LAC, but not vice versa.
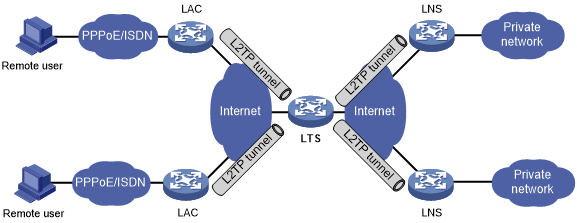
L2TP tunnel switching—Also called multihop L2TP tunneling. As shown in Figure 29, the Layer 2 tunnel switch (LTS) terminates L2TP packets from each LAC as an LNS. It then sends these packets to a destination LNS as an LAC.
L2TP tunnel switching has the following features:
Simplified configuration and deployment—When LACs and LNSs are in different management domains:
All LACs consider the LTS as an LNS and do not need to differentiate LNSs on the network.
All LNSs consider the LTS as an LAC and are not affected by the addition or deletion of LACs.
L2TP tunnel sharing—Different users can share the same L2TP tunnel between the LAC and the LTS. The LTS distributes data of different users to different LNSs.
Figure 29: L2TP tunnel switching network diagram