Publickey authentication enabled SFTP client configuration example
Network requirements
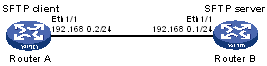
As shown in Figure 129, you can log in to Router B through the SFTP client that runs on Router A. Router B acts as the SFTP server, adopting publickey authentication and the RSA public key algorithm.
Figure 129: Network diagram
Configuration considerations
In the server configuration, the client public key is required. Use the client software to generate an RSA key pair on the client before configuring the SFTP server.
Configuration procedure
Configure the SFTP client:
# Configure an IP address for interface Ethernet 1/1.
<RouterA> system-view [RouterA] interface ethernet 1/1 [RouterA-Ethernet1/1] ip address 192.168.0.2 255.255.255.0 [RouterA-Ethernet1/1] quit
# Generate the RSA key pairs.
[RouterA] public-key local create rsa The range of public key size is (512 ~ 2048). NOTES: If the key modulus is greater than 512, It will take a few minutes. Press CTRL+C to abort. Input the bits of the modulus[default = 1024]: Generating Keys... ++++++++ ++++++++++++++ +++++ ++++++++
# Export the host public key to file pubkey.
[RouterA] public-key local export rsa ssh2 pubkey [RouterA] quit
# Transmit the public key file to the server through FTP or TFTP . (Details not shown.)
Configure the SFTP server:
# Generate the RSA key pairs.
<RouterB> system-view [RouterB] public-key local create rsa The range of public key size is (512 ~ 2048). NOTES: If the key modulus is greater than 512, It will take a few minutes. Press CTRL+C to abort. Input the bits of the modulus[default = 1024]: Generating Keys... ++++++++ ++++++++++++++ +++++ ++++++++
# Generate a DSA key pair.
[RouterB] public-key local create dsa The range of public key size is (512 ~ 2048). NOTES: If the key modulus is greater than 512, It will take a few minutes. Press CTRL+C to abort. Input the bits of the modulus[default = 1024]: Generating Keys... ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++++++++++++++++++++++
# Enable the SSH server function.
[RouterB] ssh server enable
# Enable the SFTP server function.
[RouterB] sftp server enable
# Configure an IP address for interface Ethernet 1/1. The client uses this address as the destination address of the SSH connection.
[RouterB] interface ethernet 1/1 [RouterB-Ethernet1/1] ip address 192.168.0.1 255.255.255.0 [RouterB-Ethernet1/1] quit
# Set the authentication mode of the user interfaces to AAA.
[RouterB] user-interface vty 0 4 [RouterB-ui-vty0-4] authentication-mode scheme
# Enable the user interfaces to support SSH.
[RouterB-ui-vty0-4] protocol inbound ssh [RouterB-ui-vty0-4] quit
# Import the peer public key from the file pubkey, and name it RouterKey.
[RouterB] public-key peer RouterKey import sshkey pubkey
# Create an SSH user client001 with the service type SFTP, authentication method publickey, public key RouterKey, and working folder cf:/.
[RouterB] ssh user client001 service-type sftp authentication-type publickey assign publickey RouterKey work-directory cf:/
Establish a connection between the SFTP client and the SFTP server:
# Establish a connection to the SFTP server and enter SFTP client view.
<RouterA> sftp 192.168.0.1 identity-key rsa Input Username: client001 Trying 192.168.0.1 ... Press CTRL+K to abort Connected to 192.168.0.1 ... The Server is not authenticated. Continue? [Y/N]:y Do you want to save the server public key? [Y/N]:n sftp-client>
# Display files under the current directory of the server, delete file z, and verify the result.
sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg -rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub -rwxrwxrwx 1 noone nogroup 0 Sep 01 08:00 z sftp-client> delete z The following File will be deleted: /z Are you sure to delete it? [Y/N]:y This operation might take a long time.Please wait... File successfully Removed sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg -rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
# Add a directory named new1 and verify the result.
sftp-client> mkdir new1 New directory created sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg -rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub drwxrwxrwx 1 noone nogroup 0 Sep 02 06:30 new1
# Rename the directory new1 to new2 and verify the result.
sftp-client> rename new1 new2 File successfully renamed sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg -rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub drwxrwxrwx 1 noone nogroup 0 Sep 02 06:33 new2
# Download the pubkey2 file from the server and save it as local file public.
sftp-client> get pubkey2 public Remote file:/pubkey2 ---> Local file: public Downloading file successfully ended
# Upload a local file named pu to the server, save it as puk, and verify the result.
sftp-client> put pu puk Local file:pu ---> Remote file: /puk Uploading file successfully ended sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg -rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new drwxrwxrwx 1 noone nogroup 0 Sep 02 06:33 new2 -rwxrwxrwx 1 noone nogroup 283 Sep 02 06:35 pub -rwxrwxrwx 1 noone nogroup 283 Sep 02 06:36 puk sftp-client>
# Exit SFTP client view.
sftp-client> quit Bye Connection closed. <RouterA>