L2TP-based EAD configuration example
Network requirements
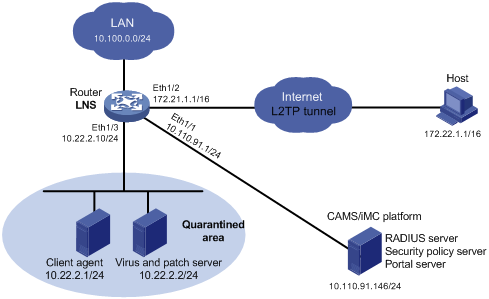
As shown in Figure 100, in the public network, the Host communicates with the LNS at Layer 3 through an L2TP tunnel. Both the security policy server and the RADIUS server are hosted by the CAMS/IMC Platform. The client agent and the virus and patch server reside in the quarantined area.
After you establish L2TP connections between remote users on the host and the LNS, the LNS assigns IP addresses in subnet 10.200.1.0/24 to the remote users on the host. The host must pass identity authentication and security check to access network resources. If the host fails to pass security authentication, it can access only the virus and patch server.
Figure 100: Network diagram
Configuration procedure
Configure the router:
# Assign an IP address to Ethernet 1/1, which is connected to the CAMS/IMC server.
<Router> system-view [Router] interface ethernet1/1 [Router-Ethernet1/1] ip address 10.110.91.1 255.255.255.0 [Router-Ethernet1/1] quit
# Assign an IP address to Ethernet 1/2, which is connected to the iNode client.
[Router] interface ethernet1/2 [Router-Ethernet1/2] ip address 172.21.1.1 255.255.0.0 [Router-Ethernet1/2] quit
# Assign an IP address to Ethernet 1/3.
[Router] interface ethernet1/3 [Router-Ethernet1/3] ip address 10.22.2.10 255.255.255.0 [Router-Ethernet1/3] quit
# Configure a RADIUS scheme that uses the CAMS/IMC server, setting the IP address to 10.110.91.146/24, and the keys to sysname.
[Router] radius scheme cams [Router-radius-cams] server-type extended [Router-radius-cams] primary authentication 10.110.91.146 [Router-radius-cams] primary accounting 10.110.91.146 [Router-radius-cams] key authentication sysname [Router-radius-cams] key accounting sysname [Router-radius-cams] quit
# Configure domain system to use the RADIUS scheme for PPP user authentication and accounting, and use the IP address pool 10.200.1.0/24 to assign IP addresses to remote hosts.
[Router] domain system [Router-isp-system] authentication ppp radius-scheme cams [Router-isp-system] ip pool 1 10.200.1.2 10.200.1.254 [Router-isp-system] quit
# Configure the IP address of the VT interface, enable PAP authentication on this interface, specify the address pool to be used to assign addresses for PPP users, enable L2TP access based EAD, and set the fragment match mode to exactly.
[Router] interface virtual-template 1 [Router-Virtual-Template1] ip address 10.200.1.1 255.255.255.0 [Router-Virtual-Template1] ppp authentication-mode pap [Router-Virtual-Template1] remote address pool 1 [Router-Virtual-Template1] ppp access-control enable [Router-Virtual-Template1] ppp access-control match-fragments exactly [Router-Virtual-Template1] quit
# Enable the L2TP service, configure an L2TP group, configure the local tunnel name as LNS, and disable tunnel authentication.
[Router] l2tp enable [Router] l2tp-group 1 [Router-l2tp1] tunnel name LNS [Router-l2tp1] undo tunnel authentication [Router-l2tp1] allow l2tp virtual-template 1 [Router-l2tp1] quit
# Enable firewall, specify the default filtering action as denying packets, and enable fragment inspection.
[Router] firewall enable [Router] firewall default deny [Router] firewall fragments-inspect
# Configure security ACL 2000 so that users passing security authentication can access the Internet.
[Router] acl number 2000 [Router-acl-basic-2000] rule 0 permit [Router-acl-basic-2000] quit
# Configure isolation ACL 3000 so that users failing security authentication can access only the quarantine area 10.22.2.0/24.
[Router] acl number 3000 [Router-acl-adv-3000] rule 0 permit ip destination 10.22.2.0 0.0.0.255
Configure the CAMS/IMC server.
Specify ACL 2000 as the security ACL and ACL 3000 as the isolation ACL in the security policy for the user.
For more configuration information, see the related CAMS/IMC documentation.