L2TP tunneling modes and tunnel establishment process
Three typical L2TP tunneling modes
Typical L2TP tunneling modes include the following:
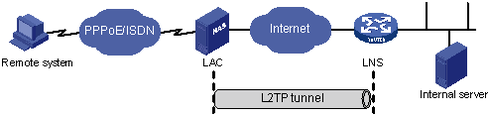
NAS-initiated—In Figure 91, a remote system dials in to the LAC through a PPPoE/ISDN network, and the LAC initiates a tunneling request to the LNS over the Internet. The LNS assigns a private IP address to the remote system. Authentication and accounting of the remote system can be implemented on the LAC or on the LNS.
Figure 91: NAS-initiated tunneling mode
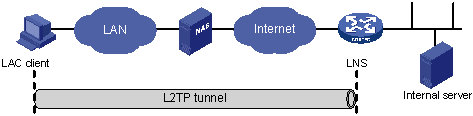
Client-initiated—In Figure 92, after being permitted to access the Internet, a remote system running the L2TP client application (LAC client) directly initiates a tunneling request to the LNS without any dedicated LAC device. The LNS assigns the LAC client a private IP address.
A LAC client needs a public network address to communicate with the LNS through the Internet.
Figure 92: Client-initiated tunneling mode
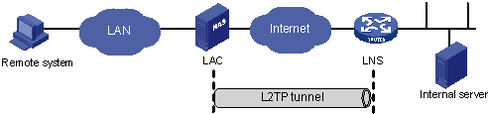
LAC-auto-initiated—In NAS-initiated mode, a remote system must successfully dial in to the LAC through PPPoE or ISDN to trigger the LAC to initiate a tunneling request to the LNS.
In LAC-auto-initiated mode, you can create a virtual PPP user and use the l2tp-auto-client enable command on the LAC. Then, the LAC automatically initiates a tunneling request to the LNS to establish an L2TP tunnel for the virtual PPP user. When a remote system accesses the internal network, the LAC forwards data through the L2TP tunnel. In this mode, the connection between a remote system and the LAC is not confined to a dial-up connection and can be any IP-based connection.
Figure 93: LAC-auto-initiated tunneling mode
L2TP tunnel establishment process
Figure 94: Typical L2TP network
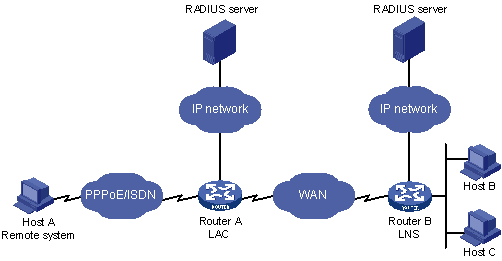
Figure 95 shows an L2TP call's setup procedure in NAS-initiated mode.
Figure 95: L2TP call setup procedure
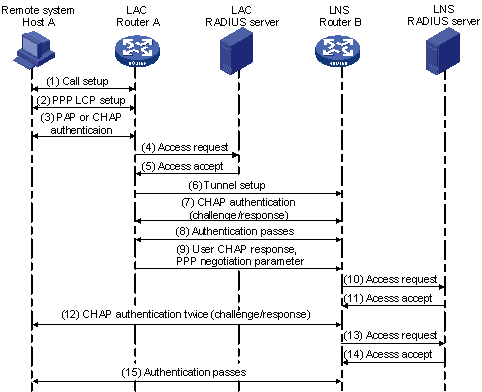
An L2TP call is set up by using the following procedure:
A remote user on Host A places a PPP call.
Host A and the LAC (Router A) perform PPP LCP negotiation.
The LAC authenticates the remote user by using the PAP, CHAP, or MS-CHAP.
The LAC sends the authentication information (the username and password) to its RADIUS server for authentication.
The LAC RADIUS server authenticates the user.
If the user passes authentication, the LAC initiates a tunneling request to the LNS.
If tunnel authentication is required, the LAC sends a CHAP challenge to the LNS. The LNS returns a CHAP response and sends its CHAP challenge to the LAC. Accordingly, the LAC returns a CHAP response to the LNS.
The tunnel passes authentication.
The LAC sends the CHAP response, response identifier, and PPP negotiation parameters of the user to the LNS.
The LNS sends an access request to its RADIUS server for authentication.
The RADIUS server authenticates the access request and returns a response if the user passes authentication.
If the LNS is configured to perform a mandatory CHAP authentication for the user, the LNS sends a CHAP challenge to the user and the user returns a CHAP response.
The LNS resends the access request to its RADIUS server for authentication.
The RADIUS server authenticates the access request and returns a response if the user passes authentication.
The LNS assigns an internal IP address to the remote user. The user can now access the internal resources of the enterprise network.