RADIUS server feature of the device
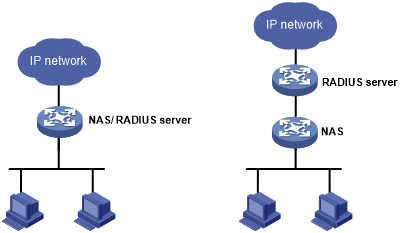
Typically, the RADIUS server runs on a computer or workstation, and the RADIUS client runs on a NAS. You can also use the device as a RADIUS server, as shown in Figure 8. This deployment is typically used for a cluster, where you can configure the cluster management device as a RADIUS server to cooperate with access-layer cluster member devices to provide authentication and authorization.
Figure 8: Devices functioning as a RADIUS server
The device can serve as a RADIUS server to provide the following functions:
User information management:
You can create, modify, and delete user information, including the username, password, authority, lifetime, and user description.
RADIUS client information management:
You can create and delete RADIUS clients, which are identified by IP address and are configured with attributes such as a shared key. You can configure the RADIUS server to process the RADIUS packets from the clients only within the specified management range. Shared keys are used to ensure secure communication between a RADIUS client and the RADIUS server.
RADIUS authentication and authorization:
With the RADIUS server enabled, the device checks whether or not the client of an incoming RADIUS packet is under its management. If yes, it verifies the packet validity by using the shared key, checks whether there is an account with the username, whether the password is correct, and whether the user attributes meet the requirements defined on the RADIUS server (for example, whether the account has expired). Then, the RADIUS server assigns the corresponding authority to the client if the authentication succeeds, or denies the client if the authentication fails.
![[NOTE: ]](images/note.png) | NOTE: A RADIUS server running the standard RADIUS protocol listens on UDP port 1812 for authentication requests, but an HPE device listens on UDP port 1645 instead when acting as the RADIUS server. Specify 1645 as the authentication port number on the RADIUS client when you use an HPE device as the RADIUS server. | |