RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a distributed information interaction protocol that uses a client/server model. It can protect networks against unauthorized access and is often used in network environments that require both high security and remote user access.
RADIUS uses UDP port 1812 for authentication and UDP port 1813 for accounting.
RADIUS was originally designed for dial-in user access. With the addition of new access methods, RADIUS has been extended to support additional access methods, including Ethernet and ADSL. RADIUS provides access authentication, authorization, and accounting services. The accounting function collects and records network resource usage information.
Client/server model
The RADIUS client runs on every NAS on the network to pass user information to the RADIUS server and determines to reject or accept each access request based on the server response.
The RADIUS server runs on the computer or workstation at the network center and maintains information related to user authentication and network access. It receives connection requests, authenticates users, and returns access control information (for example, rejecting or accepting the user access request) to the client.
The RADIUS server typically maintains the following databases: Users, Clients, and Dictionary. See Figure 2.
Figure 2: RADIUS server databases
Users—Stores user information, such as the usernames, passwords, applied protocols, and IP addresses.
Clients—Stores information about RADIUS clients, such as shared keys and IP addresses.
Dictionary—Stores RADIUS protocol attributes and their values.
Security and authentication mechanisms
The RADIUS client and the RADIUS server use a shared key to authenticate RADIUS packets and encrypt user passwords exchanged between them. For security, this key must be manually configured on the client and the server.
RADIUS servers support multiple authentication protocols, including PAP and CHAP. A RADIUS server can also act as the client of another AAA server to provide authentication proxy services.
Basic RADIUS message exchange process
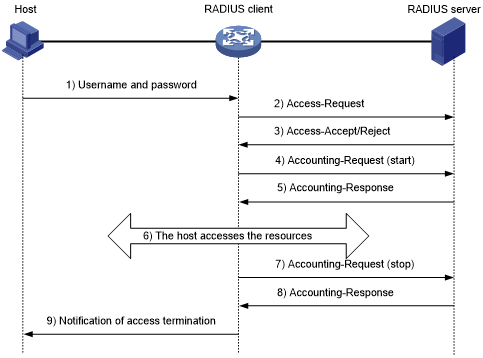
Figure 3 illustrates the interactions between the host, the RADIUS client, and the RADIUS server.
Figure 3: Basic RADIUS message exchange process
RADIUS operates in the following manner:
The host initiates a connection request that carries the user's username and password to the RADIUS client.
Having received the username and password, the RADIUS client sends an authentication request (Access-Request) to the RADIUS server, with the user password encrypted by using the MD5 algorithm and the shared key.
The RADIUS server authenticates the username and password. If the authentication succeeds, the server returns an Access-Accept message containing the user's authorization information. If the authentication fails, the server returns an Access-Reject message.
The RADIUS client permits or denies the user according to the returned authentication result. If it permits the user, it sends a start-accounting request (Accounting-Request) to the RADIUS server.
The RADIUS server returns an acknowledgement (Accounting-Response) and starts accounting.
The user accesses the network resources.
The host requests the RADIUS client to tear down the connection and the RADIUS client sends a stop-accounting request (Accounting-Request) to the RADIUS server.
The RADIUS server returns an acknowledgement (Accounting-Response) and stops accounting for the user.
RADIUS packet format
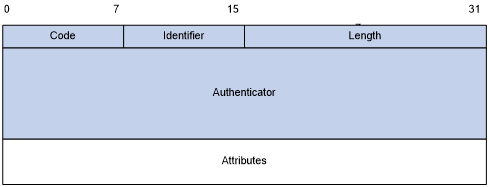
RADIUS uses UDP to transmit messages. To ensure smooth message exchange between the RADIUS server and the client, RADIUS uses timer management, retransmission, and a backup server mechanism. Figure 4 shows the RADIUS packet format.
Figure 4: RADIUS packet format
Descriptions of the fields are as follows:
The Code field (1 byte long) indicates the type of the RADIUS packet.
Table 1: Main values of the Code field
Code | Packet type | Description |
|---|---|---|
1 | Access-Request | From the client to the server. A packet of this type carries user information for the server to authenticate the user. It must contain the User-Name attribute and can optionally contain the attributes of NAS-IP-Address, User-Password, and NAS-Port. |
2 | Access-Accept | From the server to the client. If all attribute values carried in the Access-Request are acceptable, the authentication succeeds, and the server sends an Access-Accept response. |
3 | Access-Reject | From the server to the client. If any attribute value carried in the Access-Request is unacceptable, the authentication fails, and the server sends an Access-Reject response. |
4 | Accounting-Request | From the client to the server. A packet of this type carries user information for the server to start or stop accounting for the user. The Acct-Status-Type attribute in the packet indicates whether to start or stop accounting. |
5 | Accounting-Response | From the server to the client. The server sends a packet of this type to notify the client that it has received the Accounting-Request and has successfully recorded the accounting information. |
The Identifier field (1 byte long) is used to match request packets and response packets and to detect duplicate request packets. Request and response packets of the same type have the same identifier.
The Length field (2 bytes long) indicates the length of the entire packet, including the Code, Identifier, Length, Authenticator, and Attributes fields. Bytes beyond this length are considered padding and are ignored at the receiver. If the length of a received packet is less than this length, the packet is dropped. The value of this field is in the range 20 to 4096.
The Authenticator field (16 bytes long) is used to authenticate responses from the RADIUS server and to encrypt user passwords. There are two types of authenticators: request authenticator and response authenticator.
The Attributes field (variable in length) carries the specific authentication, authorization, and accounting information that defines the configuration details of the request or response. This field may contain multiple attributes, each with three sub-fields:
Type—(1 byte long) Type of the attribute. It is in the range of 1 to 255. Commonly used RADIUS attributes are defined in RFC 2865, RFC 2866, RFC 2867, and RFC 2868. Table 2 shows a list of the attributes. For more information, see "Commonly used standard RADIUS attributes."
Length—(1 byte long) Length of the attribute in bytes, including the Type, Length, and Value sub-fields.
Value—(Up to 253 bytes) Value of the attribute. Its format and content depend on the Type and Length sub-fields.
Table 2: Commonly used RADIUS attributes
No. | Attribute | No. | Attribute |
|---|---|---|---|
1 | User-Name | 45 | Acct-Authentic |
2 | User-Password | 46 | Acct-Session-Time |
3 | CHAP-Password | 47 | Acct-Input-Packets |
4 | NAS-IP-Address | 48 | Acct-Output-Packets |
5 | NAS-Port | 49 | Acct-Terminate-Cause |
6 | Service-Type | 50 | Acct-Multi-Session-Id |
7 | Framed-Protocol | 51 | Acct-Link-Count |
8 | Framed-IP-Address | 52 | Acct-Input-Gigawords |
9 | Framed-IP-Netmask | 53 | Acct-Output-Gigawords |
10 | Framed-Routing | 54 | (unassigned) |
11 | Filter-ID | 55 | Event-Timestamp |
12 | Framed-MTU | 56-59 | (unassigned) |
13 | Framed-Compression | 60 | CHAP-Challenge |
14 | Login-IP-Host | 61 | NAS-Port-Type |
15 | Login-Service | 62 | Port-Limit |
16 | Login-TCP-Port | 63 | Login-LAT-Port |
17 | (unassigned) | 64 | Tunnel-Type |
18 | Reply-Message | 65 | Tunnel-Medium-Type |
19 | Callback-Number | 66 | Tunnel-Client-Endpoint |
20 | Callback-ID | 67 | Tunnel-Server-Endpoint |
21 | (unassigned) | 68 | Acct-Tunnel-Connection |
22 | Framed-Route | 69 | Tunnel-Password |
23 | Framed-IPX-Network | 70 | ARAP-Password |
24 | State | 71 | ARAP-Features |
25 | Class | 72 | ARAP-Zone-Access |
26 | Vendor-Specific | 73 | ARAP-Security |
27 | Session-Timeout | 74 | ARAP-Security-Data |
28 | Idle-Timeout | 75 | Password-Retry |
29 | Termination-Action | 76 | Prompt |
30 | Called-Station-Id | 77 | Connect-Info |
31 | Calling-Station-Id | 78 | Configuration-Token |
32 | NAS-Identifier | 79 | EAP-Message |
33 | Proxy-State | 80 | Message-Authenticator |
34 | Login-LAT-Service | 81 | Tunnel-Private-Group-id |
35 | Login-LAT-Node | 82 | Tunnel-Assignment-id |
36 | Login-LAT-Group | 83 | Tunnel-Preference |
37 | Framed-AppleTalk-Link | 84 | ARAP-Challenge-Response |
38 | Framed-AppleTalk-Network | 85 | Acct-Interim-Interval |
39 | Framed-AppleTalk-Zone | 86 | Acct-Tunnel-Packets-Lost |
40 | Acct-Status-Type | 87 | NAS-Port-Id |
41 | Acct-Delay-Time | 88 | Framed-Pool |
42 | Acct-Input-Octets | 89 | (unassigned) |
43 | Acct-Output-Octets | 90 | Tunnel-Client-Auth-id |
44 | Acct-Session-Id | 91 | Tunnel-Server-Auth-id |
Extended RADIUS attributes
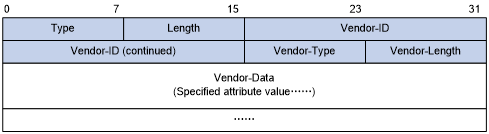
Attribute 26 (Vender-Specific), an attribute defined in RFC 2865, allows a vendor to define extended attributes to implement functions that the standard RADIUS protocol does not provide.
A vendor can encapsulate multiple sub-attributes as TLVs in attribute 26 to provide extended functions. As shown in Figure 5, a sub-attribute encapsulated in attribute 26 consists of the following parts:
Vendor-ID—ID of the vendor. Its most significant byte is 0. The other three bytes contains a code that is compliant to RFC 1700. For more information about the proprietary RADIUS sub-attributes of HPE, see "HPE proprietary RADIUS sub-attributes."
Vendor-Type—Type of the sub-attribute.
Vendor-Length—Length of the sub-attribute.
Vendor-Data—Contents of the sub-attribute.
Figure 5: Format of attribute 26