Allowing mutual access between IPv4 and IPv6 networks
Network requirements
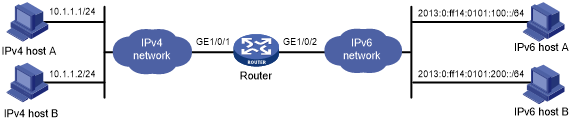
As shown in Figure 113, a company deploys both an IPv4 network and an IPv6 network.
To allow mutual access between the IPv4 network and the IPv6 network, configure the following AFT policies on the router:
Assign an IVI prefix and an IPv4 subnet to the IPv6 network. Each IPv6 host uses the IPv6 addresses formed by the IVI prefix and an IPv4 address on the IPv4 subnet.
Configure a NAT64 prefix to translate source IPv4 addresses of packets initiated by the IPv4 network to IPv6 addresses.
Figure 113: Network diagram
Configuration procedure
# Specify IP addresses for the interfaces on the router. The IPv6 addresses for IPv6 hosts are calculated by the IVI prefix 2013::/32 and IPv4 addresses in the range of 20.1.1.0/24. (Details not shown.)
# Configure IPv4 ACL 2000 to permits all IPv4 packets to pass through.
<Router> system-view [Router] acl basic 2000 [Router-acl-ipv4-basic-2000] rule permit [Router-acl-ipv4-basic-2000] quit
# Configure the router to use NAT64 prefix 2012:: 96 to translate source addresses of IPv4 packets. The router also uses the prefix to translate destination addresses of IPv6 packets.
[Router] aft prefix-nat64 2012:: 96
# Configure the router to use IVI prefix 2013:: to translate source addresses of IPv6 packets.
[Router] aft prefix-ivi 2013::
# Configure the router to use IVI prefix 2013:: to translate destination addresses of packets permitted by IPv4 ACL 2000.
[Router] aft v4tov6 destination acl number 2000 prefix-ivi 2013::
# Enable AFT on GigabitEthernet1/0/1, which is connected to the IPv4 network.
[Router] interface gigabitethernet 1/0/1 [Router-GigabitEthernet1/0/1] aft enable [Router-GigabitEthernet1/0/1] quit
# Enable AFT on GigabitEthernet1/0/2, which is connected to the IPv6 network.
[Router] interface gigabitethernet 1/0/2 [Router-GigabitEthernet1/0/2] aft enable [Router-GigabitEthernet1/0/2] quit
Verifying the configuration
# Verify the connectivity between IPv6 hosts and IPv4 hosts. This example pings IPv4 host A from IPv6 host A.
D:\>ping 2012::a01:0101 Pinging 2012::a01:0101 with 32 bytes of data: Reply from 2012::a01:0101: time=3ms Reply from 2012::a01:0101: time=3ms Reply from 2012::a01:0101: time=3ms Reply from 2012::a01:0101: time=3ms
# Display information about IPv6 AFT sessions on the router.
[Router] display aft session ipv6 verbose Initiator: Source IP/port: 2013:0:FF14:0101:0100::/0 Destination IP/port: 2012::0a01:0101/32768 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: IPV6-ICMP(58) Inbound interface: GigabitEthernet1/0/2 Responder: Source IP/port: 2012::0a01:0101/0 Destination IP/port: 2013:0:FF14:0101:0100::/33024 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: IPV6-ICMP(58) Inbound interface: GigabitEthernet1/0/1 State: ICMPV6_REPLY Application: OTHER Start time: 2014-03-13 08:52:59 TTL: 23s Initiator->Responder: 4 packets 320 bytes Responder->Initiator: 4 packets 320 bytes Total sessions found: 1
# Display information about IPv4 AFT sessions on the router.
[Router] display aft session ipv4 verbose Initiator: Source IP/port: 20.1.1.1/1025 Destination IP/port: 10.1.1.1/2048 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/2 Responder: Source IP/port: 10.1.1.1/1025 Destination IP/port: 20.1.1.1/0 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/1 State: ICMP_REPLY Application: OTHER Start time: 2014-03-13 08:52:59 TTL: 27s Initiator->Responder: 4 packets 240 bytes Responder->Initiator: 4 packets 240 bytes Total sessions found: 1