Allowing IPv4 Internet access from an IPv6 network
Network requirements
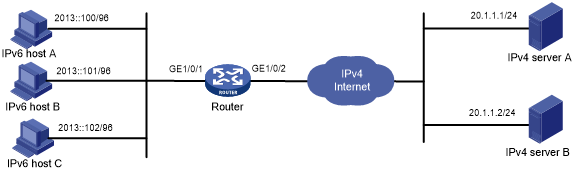
As shown in Figure 111, a company upgrades the network to IPv6 and has IPv4 addresses from 10.1.1.1 to 10.1.1.3.
To allow IPv6 hosts on subnet 2013::/96 to access the IPv4 Internet, configure the following AFT policies on the router:
Configure a NAT64 prefix to translate IPv4 addresses of IPv4 servers to IPv6 addresses.
Configure an IPv6-to-IPv4 source address dynamic translation policy to translate source IPv6 addresses of IPv6-initiated packets to IPv4 addresses in the range of 10.1.1.1 to 10.1.1.3.
Figure 111: Network diagram
Configuration process
# Specify IP addresses for the interfaces on the router. (Details not shown.)
# Create AFT address group 0, and add the address range from 10.1.1.1 to 10.1.1.3 to the group.
<Router> system-view [Router] aft address-group 0 [Router-aft-address-group-0] address 10.1.1.1 10.1.1.3 [Router-aft-address-group-0] quit
# Configure IPv6 ACL 2000 to permit IPv6 packets only from subnet 2013::/96 to pass through.
[Router] acl ipv6 basic 2000 [Router-acl-ipv6-basic-2000] rule permit source 2013:: 96 [Router-acl-ipv6-basic-2000] rule deny [Router-acl-ipv6-basic-2000] quit
# Configure the router to translate source IPv6 addresses of packets permitted by IPv6 ACL 2000 to IPv4 addresses in address group 0.
[Router] aft v6tov4 source acl ipv6 number 2000 address-group 0
# Configure the router to use NAT64 prefix 2012::/96 to translate destination IPv6 addresses of IPv6 packets.
[Router] aft prefix-nat64 2012:: 96
# Enable AFT on GigabitEthernet 1/0/1, which is connected to the IPv6 network.
[Router] interface gigabitethernet 1/0/1 [Router-GigabitEthernet1/0/1] aft enable [Router-GigabitEthernet1/0/1] quit
# Enable AFT on GigabitEthernet 1/0/2, which is connected to the IPv4 Internet.
[Router] interface gigabitethernet 1/0/2 [Router-GigabitEthernet1/0/2] aft enable [Router-GigabitEthernet1/0/2] quit
Verifying the configuration
# Verify the connectivity between IPv6 hosts and IPv4 servers. This example pings IPv4 server A from IPv6 host A.
D:\>ping 2012::20.1.1.1 Pinging 2012::20.1.1.1 with 32 bytes of data: Reply from 2012::20.1.1.1: time=3ms Reply from 2012::20.1.1.1: time=3ms Reply from 2012::20.1.1.1: time=3ms Reply from 2012::20.1.1.1: time=3ms
# Display detailed information about IPv6 AFT sessions on the router.
[Router] display aft session ipv6 verbose Initiator: Source IP/port: 2013::100/0 Destination IP/port: 2012::1401:0101/32768 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: IPV6-ICMP(58) Inbound interface: GigabitEthernet1/0/1 Responder: Source IP/port: 2012::1401:0101/0 Destination IP/port: 2013::100/33024 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: IPV6-ICMP(58) Inbound interface: GigabitEthernet1/0/2 State: ICMPV6_REPLY Application: OTHER Start time: 2014-03-13 08:52:59 TTL: 23s Initiator->Responder: 4 packets 320 bytes Responder->Initiator: 4 packets 320 bytes Total sessions found: 1
# Display detailed information about IPv4 AFT sessions on the router.
[Router] display aft session ipv4 verbose Initiator: Source IP/port: 10.1.1.1/1025 Destination IP/port: 20.1.1.1/2048 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/1 Responder: Source IP/port: 20.1.1.1/1025 Destination IP/port: 10.1.1.1/0 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/2 State: ICMP_REPLY Application: OTHER Start time: 2014-03-13 08:52:59 TTL: 27s Initiator->Responder: 4 packets 240 bytes Responder->Initiator: 4 packets 240 bytes Total sessions found: 1