Twice NAT configuration example
Network requirements
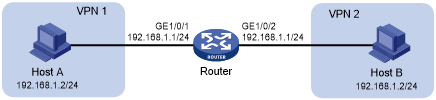
As shown in Figure 64, two departments are in different VPN instances with overlapping addresses. Configure twice NAT so that Host A and Host B in different departments can access each other.
Figure 64: Network diagram
Requirements analysis
This is a typical application of twice NAT. Both the source and destination addresses of packets between the two VPNs need to be translated. Configure static NAT on both interfaces connected to the VPNs on the NAT device.
Configuration procedure
# Specify VPN instances and IP addresses for the interfaces on the router. (Details not shown.)
# Configure a static outbound NAT mapping between 192.168.1.2 in vpn 1 and 172.16.1.2 in vpn 2.
<Router> system-view [Router] nat static outbound 192.168.1.2 vpn-instance vpn1 172.16.1.2 vpn-instance vpn2
# Configure a static outbound NAT mapping between 192.168.1.2 in vpn 2 and 172.16.2.2 in vpn 1.
[Router] nat static outbound 192.168.1.2 vpn-instance vpn2 172.16.2.2 vpn-instance vpn1
# Enable static NAT on interface GigabitEthernet 1/0/2.
[Router] interface gigabitethernet 1/0/2 [Router-GigabitEthernet1/0/2] nat static enable
# Enable static NAT on interface GigabitEthernet 1/0/1.
[Router] interface gigabitethernet 1/0/1 [Router-GigabitEthernet1/0/1] nat static enable
Verifying the configuration
# Verify that Host A and Host B can access each other. The public address for Host A is 172.16.1.2 and that for Host B is 172.16.2.2. (Details not shown.)
# Display all NAT configuration and statistics.
[Router] display nat all
Static NAT mappings:
Totally 2 outbound static NAT mappings.
IP-to-IP:
Local IP : 192.168.1.2
Global IP : 172.16.1.2
Local VPN : vpn1
Global VPN : vpn2
Config status: Active
IP-to-IP:
Local IP : 192.168.1.2
Global IP : 172.16.2.2
Local VPN : vpn2
Global VPN : vpn1
Config status: Active
Interfaces enabled with static NAT:
Totally 2 interfaces enabled with static NAT.
Interface: GigabitEthernet1/0/1
Config status: Active
Interface: GigabitEthernet1/0/2
Config status: Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NAT mapping behavior:
Mapping mode : Address and Port-Dependent
ACL : ---
Config status: Active
NAT ALG:
DNS : Enabled
FTP : Enabled
H323 : Enabled
ICMP-ERROR : Enabled
ILS : Enabled
MGCP : Enabled
NBT : Enabled
PPTP : Enabled
RSH : Enabled
RTSP : Enabled
SCCP : Enabled
SIP : Enabled
SQLNET : Enabled
TFTP : Enabled
XDMCP : Enabled
# Display NAT session information generated when Host A accesses Host B.
[Router] display nat session verbose Initiator: Source IP/port: 192.168.1.2/42496 Destination IP/port: 172.16.2.2/2048 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: vpn1/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/1 Responder: Source IP/port: 192.168.1.2/42496 Destination IP/port: 172.16.1.2/0 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: vpn2/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/2 State: ICMP_REPLY Application: INVALID Start time: 2012-08-16 09:30:49 TTL: 27s Initiator->Responder: 5 packets 420 bytes Responder->Initiator: 5 packets 420 bytes Total sessions found: 1