802.1X EAP-PEAP RADIUS authentication configuration example
Network requirements
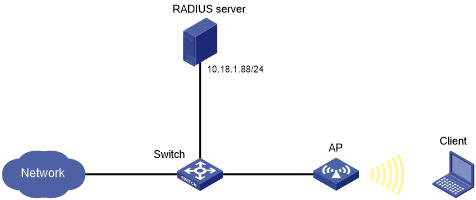
As shown in Figure 34, configure the AP to perform 802.1X RADIUS authentication for the client by using EAP-PEAP.
Figure 35: Network diagram
Configuration procedure
Configure the AP:
Configure 802.1X and the RADIUS scheme:
# Configure the AP to use EAP relay to authenticate 802.1X clients.
<AP> system-view [AP] dot1x authentication-method eap
# Create a RADIUS scheme.
[AP] radius scheme imcc
# Specify the primary authentication server and the primary accounting server.
[AP-radius-imcc] primary authentication 10.18.1.88 1812 [AP-radius-imcc] primary accounting 10.18.1.88 1813
# Set the authentication and accounting shared keys to 12345678 in plain text for secure RADIUS communication with the server.
[AP-radius-imcc] key authentication simple 12345678 [AP-radius-imcc] key accounting simple 12345678
# Exclude domain names from the usernames sent to the RADIUS server.
[AP-radius-imcc] user-name-format without-domain [AP-radius-imcc] quit
Configure AAA methods for the ISP domain:
# Create an ISP domain named imc.
[AP] domain imc
# Configure the ISP domain to use RADIUS scheme imcc for authentication, authorization, and accounting of LAN clients.
[AP-isp-imc] authentication lan-access radius-scheme imcc [AP-isp-imc] authorization lan-access radius-scheme imcc [AP-isp-imc] accounting lan-access radius-scheme imcc [AP-isp-imc] quit
Configure a service template:
# Create a service template named wlas_imc_peap.
[AP] wlan service-template wlas_imc_peap
# Set the authentication mode to 802.1X.
[AP-wlan-st-wlas_imc_peap] client-security authentication-mode dot1x
# Specify ISP domain imc for the service template.
[AP-wlan-st-wlas_imc_peap] dot1x domain imc
# Set the SSID to wlas_imc_peap.
[AP-wlan-st-wlas_imc_peap] ssid wlas_imc_peap
# Set the AKM mode to 802.1X.
[AP-wlan-st-wlas_imc_peap] akm mode dot1x
# Set the CCMP cipher suite.
[AP-wlan-st-wlas_imc_peap] cipher-suite ccmp
# Enable the RSN-IE in the beacon and probe responses.
[AP-wlan-st-wlas_imc_peap] security-ie rsn
# Enable the service template.
[AP-wlan-st-wlas_imc_tls] service-template enable [AP-wlan-st-wlas_imc_tls] quit
Bind the service template to an AP radio.
[AP] interface wlan-radio 0/1 [AP-WLAN-Radio0/1] undo shutdown [AP-WLAN-Radio0/1] service template wlas_local_chap [AP-WLAN-Radio0/1] quit
Configure the RADIUS server:
In this example, the RADIUS server runs IMC PLAT 7.1 and IMC UAM 7.1, and the EAP-PEAP certificate has been installed.
# Add an access device:
Click the User tab.
From the navigation tree, select User Access Policy > Access Device Management > Access Device.
Click Add.
The Add Access Device page appears.
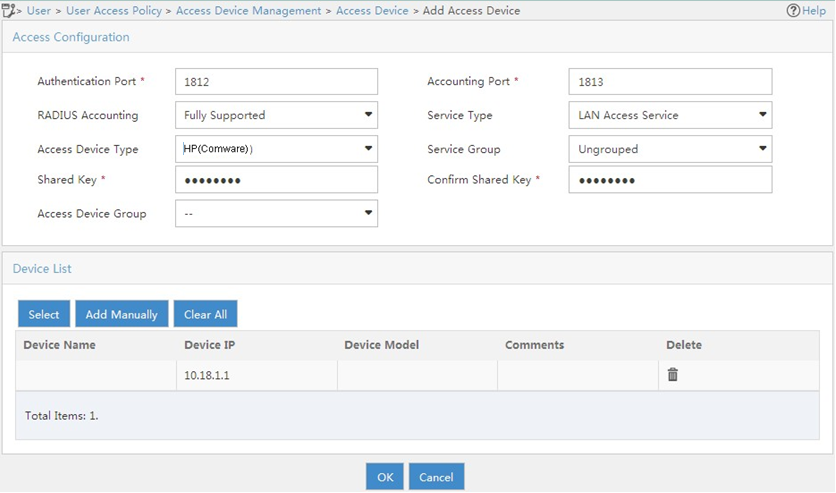
In the Access Configuration area, configure the following parameters, as shown in Figure 35:
Enter 12345678 in the Shared Key and Confirm Shared Key fields.
Use the default values for other parameters.
In the Device List area, click Select or Add Manually to add the device at 10.18.1.1 as an access device.
Click OK.
Figure 36: Adding an access device
# Add an access policy:
Click the User tab.
From the navigation tree, select User Access Policy > Access Policy.
Click Add.
On the Add Access Policy page, configure the following parameters, as shown in Figure 36:
Enter dot1x in the Access Policy Name field.
Select EAP for the Certificate Authentication field
Select EAP-PEAP Auth from the Certificate Type list, and select MS-CHAPV2 Auth from the Certificate Sub-Type list.
The certificate sub-type on the IMC server must be the same as the identity authentication method configured on the client.
Click OK.
Figure 37: Adding an access policy

# Add an access service:
Click the User tab.
From the navigation tree, select User Access Policy > Access Service.
Click Add.
On the Add Access Service page, configure the following parameters, as shown in Figure 37:
Enter dot1x in the Service Name field.
Select dot1x from the Default Access Policy list.
Click OK.
Figure 38: Adding an access service

# Add an access user:
Click the User tab.
From the navigation tree, select Access User > All Access Users.
The access user list appears.
Click Add.
The Add Access User page appears.
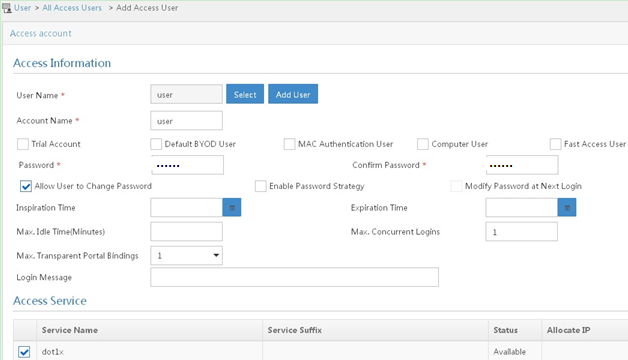
In the Access Information area, configure the following parameters, as shown in Figure 38:
Click Select or Add User to associate the user with IMC Platform user user.
Enter user in the Account Name field.
Enter dot1x in the Password and Confirm Password fields.
In the Access Service area, select dot1x from the list.
Click OK.
Figure 39: Adding an access user account
Configure the WLAN client:
The WLAN client has been installed with the EAP-PEAP certificate.
To configure the WLAN client, perform the following tasks (details not shown):
Select PEAP for identity authentication.
Disable the client from verifying the server certificate.
Disable the client from automatically using the Windows login name and password.
Verifying the configuration
On the client, verify that you can use username user and password dot1x to access the network. (Details not shown.)
On the AP, perform the following tasks to verify that the user has passed authentication and come online:
# Display online 802.1X client information.
[AP] display dot1x connection User MAC address : 0023-8933-2090 AP name : ap1 Radio ID : 1 SSID : wlas_imc_peap BSSID : 000f-e201-0003 User name : user Authentication domain : imc Authentication method : EAP Initial VLAN : 1 Authorization VLAN : N/A Authorization ACL number : N/A Authorization user profile : N/A Termination action : Default Session timeout period : 6001 s Online from : 2014/04/18 09:25:18 Online duration : 0h 1m 1s Total connections: 1.
# Display WLAN client information.
[AP] display wlan client Total number of clients : 1 MAC address Username APID/RID IP address IPv6 address VLAN 0023-8933-2090 user 1/1 10.18.1.100 1