802.1X authentication process
The authenticator uses EAP relay or EAP termination to communicate with the RADIUS server.
EAP relay
In this mode, the authenticator uses EAPOR packets to send authentication information to the RADIUS server. The RADIUS server must support the EAP-Message and Message-Authenticator attributes, and must use the same authentication method as the client. For the authenticator, you only need to use the dot1x authentication-method eap command to enable EAP relay.
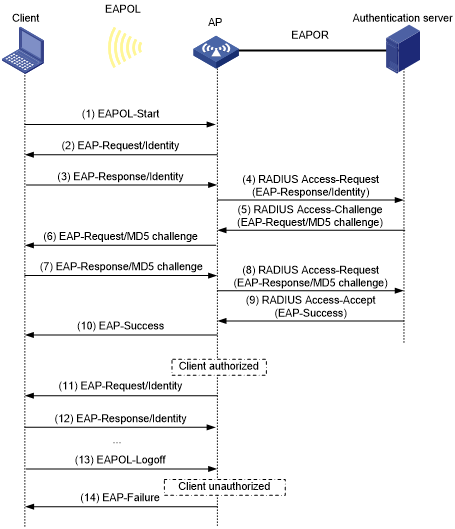
Figure 31 shows the basic 802.1X authentication process in EAP relay mode. In this example, EAP-MD5 is used.
Figure 32: 802.1X authentication process in EAP relay mode
The following steps describe the 802.1X authentication process:
When a user launches the 802.1X client and enters a registered username and password, the 802.1X client sends an EAPOL-Start packet to the authenticator.
For information about the client and AP association, see "Configuring WLAN security."
The authenticator responds with an EAP-Request/Identity packet to request for the username.
The client sends the username in an EAP-Response/Identity packet to the authenticator.
The authenticator relays the EAP-Response/Identity packet in a RADIUS Access-Request packet to the authentication server.
The authentication server uses the username in the RADIUS Access-Request to search its user database. If a matching entry is found, the server uses a randomly generated challenge (EAP-Request/MD5-challenge) to encrypt the password in the entry. Then, the server sends the challenge in a RADIUS Access-Challenge packet to the authenticator.
The authenticator transmits the EAP-Request/MD5-Challenge packet to the client.
The client uses the received challenge to encrypt the password, and sends the encrypted password in an EAP-Response/MD5-Challenge packet to the authenticator.
The authenticator relays the EAP-Response/MD5-Challenge packet in a RADIUS Access-Request packet to the authentication server.
The authentication server compares the received encrypted password with the encrypted password it generated at step 5. If the two passwords are identical, the server considers the client valid and sends a RADIUS Access-Accept packet to the authenticator.
Upon receiving the RADIUS Access-Accept packet, the authenticator allows the client to access the network.
After the client comes online, the authenticator periodically sends handshake requests to examine whether the client is still online.
Upon receiving a handshake request, the client returns a response. If the client fails to return a response after a number of consecutive handshake attempts (two by default), the authenticator logs off the client. This handshake mechanism enables timely release of the network resources used by 802.1X clients that have abnormally gone offline.
The client sends an EAPOL-Logoff packet to request a logoff from the authenticator.
In response to the EAPOL-Logoff packet, the authenticator sends an EAP-Failure packet to the client.
EAP termination
In this mode, the authenticator performs the following operations:
Terminates the EAP packets received from the client.
Encapsulates the client authentication information in standard RADIUS packets.
Uses PAP or CHAP to communicate with the RADIUS server.
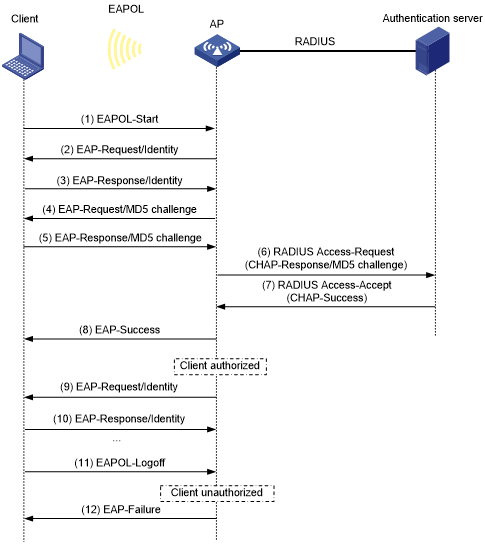
Figure 32 shows the basic 802.1X authentication process in EAP termination mode. In this example, CHAP authentication is used.
Figure 33: 802.1X authentication process in EAP termination mode
In EAP termination mode, the authentication device rather than the authentication server generates an MD5 challenge for password encryption. The authentication device then sends the MD5 challenge together with the username and encrypted password in a standard RADIUS packet to the RADIUS server.