ASPF configuration example
Network requirements
Configure an ASPF policy on Router A to inspect the FTP and HTTP traffic flows passing through Router A.
Only return packets for FTP and HTTP connections initiated by users on the internal network are permitted to pass through Router A and get into the internal network. All other types of packets are blocked. In addition, this ASPF policy should be able to block Java applets carried in HTTP packets from the server 2.2.2.11.
This example is suitable for a scenario where local users need to gain access to remote servers.
Figure 115: Network diagram
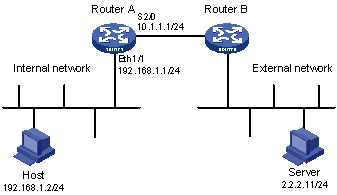
Configuration procedure
# Enable the firewall function on Router A.
<RouterA> system-view [RouterA] firewall enable
# Configure ACL 3111 to prohibit all IP packets from entering into the internal network. The ASPF will create a TACL for packets permitted to pass the firewall.
[RouterA] acl number 3111 [RouterA-acl-adv-3111] rule deny ip [RouterA-acl-adv-3111] quit
# Create ACL 2001 to block Java applets from site 2.2.2.11.
[RouterA] acl number 2001 [RouterA-acl-basic-2001] rule deny source 2.2.2.11 0 [RouterA-acl-basic-2001] rule permit [RouterA-acl-basic-2001] quit
# Create an ASPF policy that checks application layer protocols FTP and HTTP, and set the idle timeout value for the two protocols to 3000 seconds.
[RouterA] aspf-policy 1 [RouterA-aspf-policy-1] detect ftp aging-time 3000 [RouterA-aspf-policy-1] detect http java-blocking 2001 aging-time 3000 [RouterA-aspf-policy-1] quit
# Apply ACL 3111 and the ASPF policy to the interface Serial 2/0.
[RouterA] interface serial 2/0 [RouterA-Serial2/0] firewall aspf 1 outbound [RouterA-Serial2/0] firewall packet-filter 3111 inbound