Configuring MPLS L3VPN over a GRE tunnel
Network requirements
CE 1 and CE 2 belong to VPN 1. The PEs support MPLS. The P router does not support MPLS and provides only IP features.
On the backbone, use a GRE tunnel to encapsulate and forward VPN packets to implement MPLS L3VPN.
Configure tunnel policies on the PEs, and specify the tunnel type for VPN traffic as GRE.
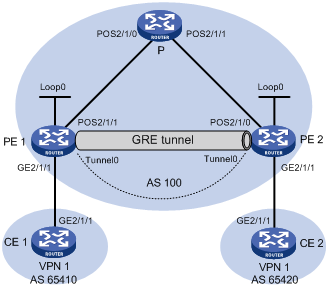
Figure 72: Network diagram
Table 14: Interface and IP address assignment
Device | Interface | IP address | Device | Interface | IP address |
|---|---|---|---|---|---|
CE 1 | GE2/1/1 | 10.1.1.1/24 | P | POS2/1/0 | 172.1.1.2/24 |
PE 1 | Loop0 | 1.1.1.9/32 | POS2/1/1 | 172.2.1.1/24 | |
GE2/1/1 | 10.1.1.2/24 | PE 2 | Loop0 | 2.2.2.9/32 | |
POS2/1/1 | 172.1.1.1/24 | GE2/1/1 | 10.2.1.2/24 | ||
Tunnel0 | 20.1.1.1/24 | POS2/1/0 | 172.2.1.2/24 | ||
CE 2 | GE2/1/1 | 10.2.1.1/24 | Tunnel0 | 20.1.1.2/24 |
Configuration procedure
Configure an IGP on the MPLS backbone to ensure IP connectivity within the backbone.
This example uses OSPF. (Details not shown.)
# Execute the display ospf peer command to verify that OSPF adjacencies in Full state have been established between PE 1, P, and PE 2. Execute the display ip routing-table command to verify that the PEs have learned the loopback route of each other. (Details not shown.)
Configure basic MPLS on the PEs:
# Configure PE 1.
<PE1> system-view [PE1] mpls lsr-id 1.1.1.9
# Configure PE 2.
<PE2> system-view [PE2] mpls lsr-id 2.2.2.9
Configure VPN instances on PEs to allow CE access, and apply tunnel policies to the VPN instances, using a GRE tunnel for VPN packet forwarding:
# Configure PE 1.
[PE1] tunnel-policy gre1 [PE1-tunnel-policy-gre1] select-seq gre load-balance-number 1 [PE1-tunnel-policy-gre1] quit [PE1] ip vpn-instance vpn1 [PE1-vpn-instance-vpn1] route-distinguisher 100:1 [PE1-vpn-instance-vpn1] vpn-target 100:1 both [PE1-vpn-instance-vpn1] tnl-policy gre1 [PE1-vpn-instance-vpn1] quit [PE1] interface gigabitethernet 2/1/1 [PE1-GigabitEthernet2/1/1] ip binding vpn-instance vpn1 [PE1-GigabitEthernet2/1/1] ip address 10.1.1.2 24 [PE1-GigabitEthernet2/1/1] quit
# Configure PE 2.
[PE2] tunnel-policy gre1 [PE2-tunnel-policy-gre1] select-seq gre load-balance-number 1 [PE2-tunnel-policy-gre1] quit [PE2] ip vpn-instance vpn1 [PE2-vpn-instance-vpn1] route-distinguisher 100:2 [PE2-vpn-instance-vpn1] vpn-target 100:1 both [PE2-vpn-instance-vpn1] tnl-policy gre1 [PE2-vpn-instance-vpn1] quit [PE2] interface gigabitethernet 2/1/1 [PE2-GigabitEthernet2/1/1] ip binding vpn-instance vpn1 [PE2-GigabitEthernet2/1/1] ip address 10.2.1.2 24 [PE2-GigabitEthernet2/1/1] quit
# Configure CE 1.
<CE1> system-view [CE1] interface gigabitethernet 2/1/1 [CE1-GigabitEthernet2/1/1] ip address 10.1.1.1 24 [CE1-GigabitEthernet2/1/1] quit
# Configure CE 2.
<CE2> system-view [CE2] interface gigabitethernet 2/1/1 [CE2-GigabitEthernet2/1/1] ip address 10.2.1.1 24 [CE2-GigabitEthernet2/1/1] quit
# Execute the display ip vpn-instance command on the PEs to display the configuration of the VPN instance, for example, on PE 1.
[PE1] display ip vpn-instance Total VPN-Instances configured : 1 VPN-Instance Name RD Create time vpn1 100:1 2012/02/13 15:59:50
# Use the ping command on the PEs to verify that the PEs can ping their attached CEs, for example, on PE 1.
[PE1] ping -vpn-instance vpn1 10.1.1.1 Ping 10.1.1.1 (10.1.1.1): 56 data bytes, press CTRL_C to break 56 bytes from 10.1.1.1: icmp_seq=0 ttl=255 time=1.000 ms 56 bytes from 10.1.1.1: icmp_seq=1 ttl=255 time=0.000 ms 56 bytes from 10.1.1.1: icmp_seq=2 ttl=255 time=0.000 ms 56 bytes from 10.1.1.1: icmp_seq=3 ttl=255 time=0.000 ms 56 bytes from 10.1.1.1: icmp_seq=4 ttl=255 time=0.000 ms --- Ping statistics for 10.1.1.1 --- 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss round-trip min/avg/max/std-dev = 0.000/0.200/1.000/0.400 ms
Establish EBGP peer relationships between PEs and CEs, and redistribute VPN routes into BGP:
# Configure CE 1.
[CE1] bgp 65410 [CE1-bgp-default] peer 10.1.1.2 as-number 100 [CE1-bgp-default] address-family ipv4 unicast [CE1-bgp-default-ipv4] peer 10.1.1.2 enable [CE1-bgp-default-ipv4] import-route direct [CE1-bgp-default-ipv4] quit [CE1-bgp-default] quit
# Configure PE 1.
[PE1] bgp 100 [PE1-bgp-default] ip vpn-instance vpn1 [PE1-bgp-default-vpn1] peer 10.1.1.1 as-number 65410 [PE1-bgp-default-vpn1] address-family ipv4 unicast [PE1-bgp-default-ipv4-vpn1] peer 10.1.1.1 enable [PE1-bgp-default-ipv4-vpn1] peer 10.1.1.1 next-hop-local [PE1-bgp-default-ipv4-vpn1] quit [PE1-bgp-default-vpn1] quit [PE1-bgp-default] quit
# Configure CE 2 and PE 2 in the same way that CE 1 and PE 1 are configured. (Details not shown.)
# Execute the display bgp peer ipv4 vpn-instance command on the PEs to verify that a BGP peer relationship in Established state has been established between a PE and a CE. (Details not shown.)
Configure an MP-IBGP peer relationship between PEs:
# Configure PE 1.
[PE1] bgp 100 [PE1-bgp-default] peer 2.2.2.9 as-number 100 [PE1-bgp-default] peer 2.2.2.9 connect-interface loopback 0 [PE1-bgp-default] address-family vpnv4 [PE1-bgp-default-vpnv4] peer 2.2.2.9 enable [PE1-bgp-default-vpnv4] quit [PE1-bgp-default] quit
# Configure PE 2 in the same way that PE 1 is configured. (Details not shown.)
# Execute the display bgp peer vpnv4 command on the PEs to verify that a BGP peer relationship in Established state has been established between the PEs. (Details not shown.)
Configure a GRE tunnel:
# Configure PE 1.
[PE1] interface tunnel 0 mode gre [PE1-Tunnel0] source loopback 0 [PE1-Tunnel0] destination 2.2.2.9 [PE1-Tunnel0] ip address 20.1.1.1 24 [PE1-Tunnel0] mpls enable [PE1-Tunnel0] quit
# Configure PE 2.
[PE2] interface tunnel 0 mode gre [PE2-Tunnel0] source loopback 0 [PE2-Tunnel0] destination 1.1.1.9 [PE2-Tunnel0] ip address 20.1.1.2 24 [PE2-Tunnel0] mpls enable [PE2-Tunnel0] quit
Verifying the configuration
# Use the following command on CE 1 to verify that the CEs have learned the interface route from each other.
[CE1] display ip routing-table Destinations : 13 Routes : 13 Destination/Mask Proto Pre Cost NextHop Interface 0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0 10.1.1.0/24 Direct 0 0 10.1.1.1 GE2/1/1 10.1.1.0/32 Direct 0 0 10.1.1.1 GE2/1/1 10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0 10.1.1.255/32 Direct 0 0 10.1.1.1 GE2/1/1 10.2.1.0/24 BGP 255 0 10.1.1.2 GE2/1/1 127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0 127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0 127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0 127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0 224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0 224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0 255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)