VPN DHCP user configuration example
Network requirements
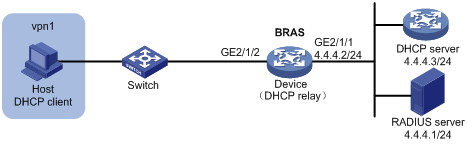
As shown in Figure 47, the host in a VPN accesses the BRAS as a DHCP user. The BRAS performs AAA for the host through the RADIUS server.
Figure 47: Network diagram
Configuration procedure
Configure the RADIUS server: (This section uses the Linux Free RADIUS server as an example.)
# Add BRAS IP address 4.4.4.2 and secret radius to the clients.conf file.
client 4.4.4.2/32 { ipaddr = 4.4.4.2 netmask=32 secret=radius }# Add host username, password, VPN, and address pool to the users user information file. The username is the host MAC address, the password is radius, the VPN is vpn1, and the address pool is pool1.
000c29a6b656 Cleartext-Password :="radius" Huawei-VPN-Instance :="vpn1", Framed-Pool := " pool1"
Configure the DHCP server:
# Enable DHCP.
<DHCP-server> system-view [DHCP-server] dhcp enable
# Create an IP address pool named pool1 and enter its view.
[DHCP-server] dhcp server ip-pool pool1
# Configure network segment 3.3.3.0/24 to the pool.
[DHCP-server-pool-pool1] network 3.3.3.0 24
# Configure IP address 3.3.3.1 as unavailable.
[DHCP-server-pool-pool1] forbidden-ip 3.3.3.1 [DHCP-server-pool-pool1] quit
# Configure a static IP address to specify the next hop for destination IP address 3.3.3.0.
[DHCP-server] ip route-static 3.3.3.0 24 4.4.4.2
Configure the BRAS:
Configure IP addresses for interfaces. (Details not shown.)
Configure a RADIUS scheme:
# Create a RADIUS scheme named rs1 and enter its view.
<Device> system-view [Device] radius scheme rs1
# Configure primary servers and keys for authentication and accounting.
[Device-radius-rs1] primary authentication 4.4.4.1 [Device-radius-rs1] primary accounting 4.4.4.1 [Device-radius-rs1] key authentication simple radius [Device-radius-rs1] key accounting simple radius
# Exclude the ISP name from the username sent to the RADIUS server.
[Device-radius-rs1] user-name-format without-domain [Device-radius-rs1] quit
Configure the ISP domain:
# Create an ISP domain named dm1 and enter its view.
[Device] domain dm1
# Configure dm1 to use RADIUS scheme rs1.
[Device-isp-dm1] authentication ipoe radius-scheme rs1 [Device-isp-dm1] authorization ipoe radius-scheme rs1 [Device-isp-dm1] accounting ipoe radius-scheme rs1 [Device-isp-dm1] quit
Configure the DHCP relay:
# Enable DHCP.
[Device] dhcp enable [Device] interface gigabitethernet 2/1/2
# Enable the DHCP relay on GigabitEthernet 2/1/2.
[Device–GigabitEthernet2/1/2] dhcp select relay [Device–GigabitEthernet2/1/2] quit
# Create an address pool named pool1 and assign pool1 to vpn1.
[Device] dhcp server ip-pool pool1 [Device-dhcp-pool-pool1] vpn-instance vpn1
# Configure a gateway IP address for the host and enable route exporting. Route exporting automatically adds the gateway IP address and related static IP address to the routing table of vpn1.
[Device-dhcp-pool-pool1] gateway-list 3.3.3.1 export-route
# Configure an IP address for the DHCP sever
[Device-dhcp-pool-pool1] remote-server 4.4.4.3
Configure IPoE:
# Enable IPoE and configure Layer 2 access mode on GigabitEthernet 2/1/2.
[Device] interface gigabitethernet 2/1/2 [Device–GigabitEthernet2/1/2] ip subscriber l2-connected enable
# Enable the DHCP user.
[Device–GigabitEthernet2/1/2] ip subscriber initiator dhcp enable
# Specify dm1 as the ISP domain.
[Device–GigabitEthernet2/1/2] ip subscriber dhcp domain dm1
# Configure plaintext password radius for authentication.
[Device–GigabitEthernet2/1/2] ip subscriber password plaintext radius [Device–GigabitEthernet2/1/2] quit
Configure a static route to direct the DHCP request from vpn1 to the DHCP server.
[Device] ip route-static vpn-instance vpn1 4.4.4.0 24 4.4.4.3 public
Configure a policy-based route to direct the traffic from the DHCP server to vpn1:
# Configure a policy named to_vpn1 with a node number of 0 and match mode of permit, and specify packets to be transmitted in vpn1.
[Device] policy-based-route to_vpn1 permit node 0 [Device-pbr-to_vpn1-0] apply access-vpn vpn-instance vpn1 [Device-pbr-to_vpn1-0] quit
# Apply to_vpn1 to GigabitEthernet 2/1/1.
[Device] interface gigabitethernet 2/1/1 [Device–GigabitEthernet2/1/1] ip policy-based-route to_vpn1 [Device–GigabitEthernet2/1/1] quit
Verifying the configuration
# Display IPoE session information to verify the configuration.
[Device] display ip subscriber session verbose Basic: Username : 000c29a6b656 Domain : dm1 VPN instance : vpn1 IP address : 3.3.3.2 MAC address : 000c-29a6-b656 Service-VLAN/Customer-VLAN : -/- Access interface : GE2/1/2 User ID : 0x380800b5 VPI/VCI(for ATM) : -/- DHCP lease : 86400 sec DHCP remain lease : 18400 sec Login time : May 9 08:56:29 2014 Online time (hh:mm:ss) : 00:16:37 Service node : Slot 1 CPU 0 Type : DHCP State : Online AAA: IP pool : pool1 Session idle time : N/A Session duration : N/A, remaining: N/A Remaining traffic : N/A Max multicast addresses : 4 Multicast address list : N/A QoS: User profile : N/A Session group profile : N/A Inbound CAR : N/A Outbound CAR : N/A Flow statistic: Uplink packets/bytes : 594341/76075648 DownLink packets/bytes : 0/0