Operating rules for source-port filters
You can configure one source-port filter for each physical port and port trunk on the switch. (See Defining and configuring named source-port filters.)
You can include all destination ports and trunks in the switch on a single source-port filter.
- Each source-port filter includes:
One source port or port trunk (trk1, trk2, ...trkn)
A set of destination ports and/or port trunks that includes all untrunked LAN ports and port trunks on the switch
An action (forward or drop) for each destination port or port trunk
When you create a source port filter, all ports and port trunks (if any) on the switch appear as destinations on the list for that filter, even if routing is disabled and separate VLANs and/or subnets exist. Where traffic would normally be allowed between ports and/or trunks, the switch automatically forwards traffic to the outbound ports and/or trunks you do not specifically configure to drop traffic. (Destination ports that comprise a trunk are listed collectively by the trunk name—such as Trk1— instead of by individual port name.)
Packets allowed for forwarding by a source-port filter are subject to the same operation as inbound packets on a port that is not configured for source-port filtering.
With multiple IP addresses configured on a VLAN, and routing enabled on the switch, a single port or trunk can be both the source and destination of packets moving between subnets in that same VLAN. In this case, you can prevent the traffic of one subnet from being routed to another subnet of the same port by configuring the port or trunk as both the source and destination for traffic to drop.
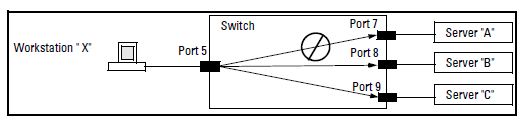
Example:
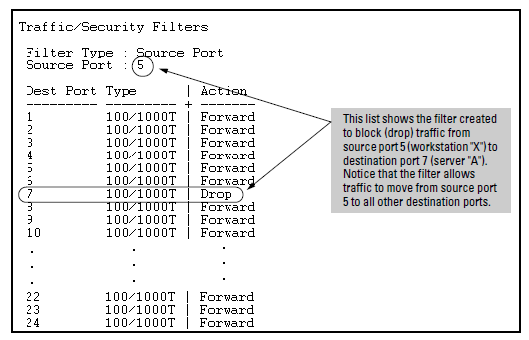
If you wanted to prevent server “A” from receiving traffic sent by workstation “X”, but do not want to prevent any other servers or end nodes from receiving traffic from workstation “X”, you would configure a filter to drop traffic from port 5 to port 7. The resulting filter would drop traffic from port 5 to port 7, but would forward all other traffic from any source port to any destination port. (See Filter blocking traffic only from Port 5 to Server A and Filter for the actions shown in Filter blocking traffic only from Port 5 to Server A.