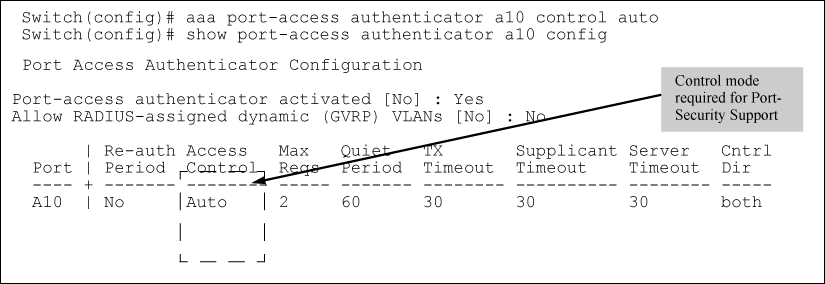
Option For Authenticator Ports: Configure Port-Security To Allow Only 802.1X-Authenticated Devices
If 802.1X authentication is disabled on a port or set to authorized (Force Authorize), the port can allow access to a non-authenticated client. Port- Security operates with 802.1X authentication only if the selected ports are configured as 802.1X with the control mode in the port-access authenticator command set to auto (the default setting). For example, if port A10 was at a non-default 802.1X setting and you wanted to configure it to support the Port-Security option, you would use the following aaa port-access command:
|
Field |
Description |
|---|---|
|
Port-access authenticator activated |
Whether 802.1X authentication is enabled or disabled on specified ports. |
|
Port |
Port number on switch. |
|
Re-auth Period |
Period of time (in seconds) after which clients connected to the port need to be reauthenticated. |
|
Access Control |
Port’s authentication mode:Auto: Network access is allowed to any connected device that supports 802.1X authentication and provides valid 802.1X credentials.Authorized: Network access is allowed to any device connected to the port, regardless of whether it meets 802.1X criteria.Unauthorized: Network access is blocked to any device connected to the port, regardless of whether the device meets 802.1X criteria. |
|
Max reqs |
Number of authentication attempts that must time-out before authentication fails and the authentication session ends. |
|
Quiet Period |
Period of time (in seconds) during which the port does not try to acquire a supplicant. |
|
TX Timeout |
Period of time (in seconds) that the port waits to retransmit the next EAPOL PDU during an authentication session. |
|
Supplicant Timeout |
Period of time (in seconds) that the switch waits for a supplicant response to an EAP request. |
|
Server Timeout |
Period of time (in seconds) that the switch waits for a server response to an authentication request. |
|
Cntrl Dir |
Direction in which flow of incoming and outgoing traffic is blocked on 802.1X-aware port that has not yet entered the authenticated state: Both: Incoming and outgoing traffic is blocked on port until authentication occurs. In: Only incoming traffic is blocked on port before authentication occurs. Outgoing traffic with unknown destination addresses is flooded on the unauthenticated 802.1X-aware port. |
Syntax
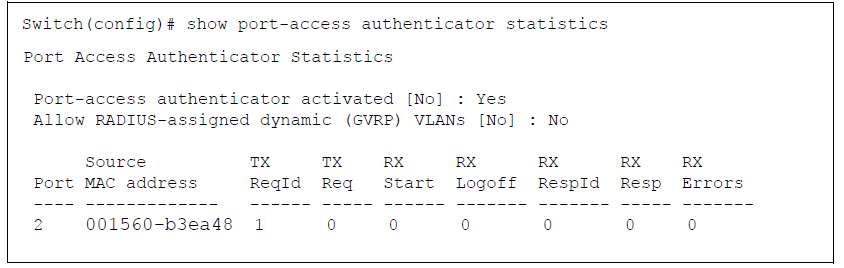
show port-access authenticator statistics [port-list]
Displays statistical information for all switch ports or specified ports that are enabled as 802.1X authenticators, including:
-
Whether port-access authentication is enabled
-
Whether RADIUS-assigned dynamic VLANs are supported
-
802.1X supplicant’s MAC address as determined by the content of the last EAPOL frame received on the port
-
802.1X traffic statistics from received and transmitted packets
-
show port-access authenticator statistics Command
Syntax
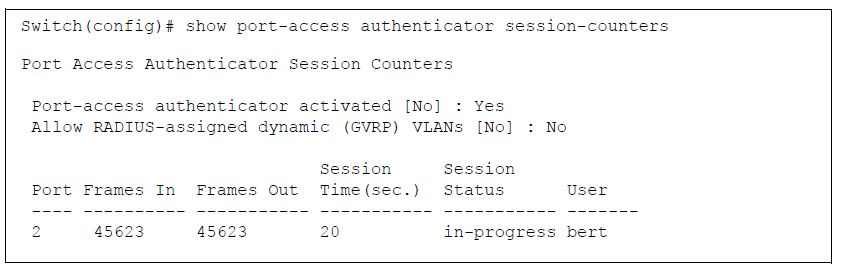
show port-access authenticator session-counters [port-list]
-
802.1X frames received and transmitted on each port
-
Duration and status of active 802.1X authentication sessions (in-progress or terminated)
-
User name of 802.1X supplicant included in 802.1X response packets, configured with the aaa port-access supplicant identity
<username>command.
show port-access authenticator session-counters Command
Syntax
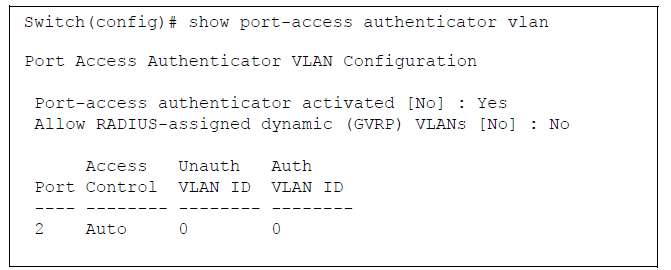
show port-access authenticator vlan [port-list]
Displays the following information on the VLANs configured for use in 802.1X port-access authentication on all switch ports, or specified ports, that are enabled as 802.1X authenticator:
-
Authentication mode used on each port, configured with the
aaa port-access authenticator controlcommand. -
VLAN ID (if any) to be used for traffic from 802.1X-authenticated clients
-
VLAN ID (if any) to be used for traffic from unauthenticated clients
802.1X configuration information for ports that are not enabled as an 802.1X authenticators is not displayed.
show port-access authenticator vlan Command
Syntax
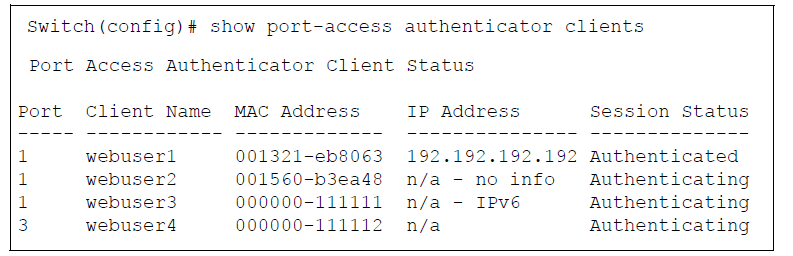
show port-access authenticator clients [port-list]
Displays the session status, name, and address for each 802.1X port-access-authenticated client on the switch. Multiple authenticated clients may be displayed for the same port. The IP address displayed is taken from the DHCP binding table (learned through the DHCP Snooping feature).
-
If DHCP snooping is not enabled on the switch, n/a (not available) is displayed for a client’s IP address.
-
If an 802.1X-authenticated client uses an IPv6 address, n/a - IPv6 is displayed.
-
If DHCP snooping is enabled but no MAC-to-IP address binding for a client is found in the DHCP binding table, n/a - no info is displayed.
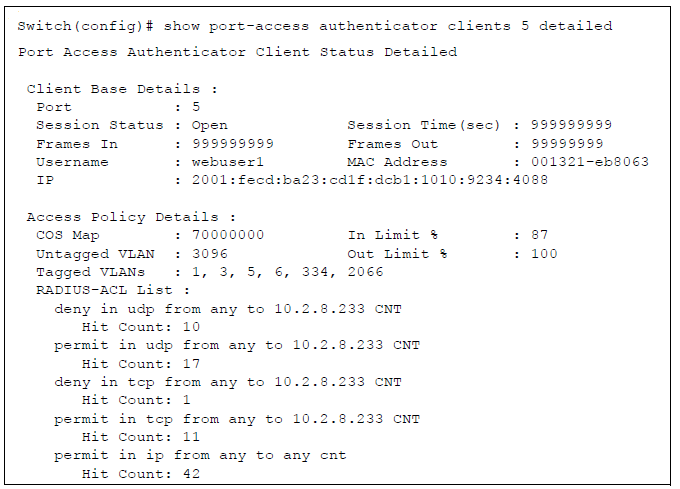
show port-access authenticator clients Command Output
Syntax
Show port-access authenticator clients <port-list> detailed
Displays detailed information on the status of 802.1X-authenticated client sessions on specified ports, including the matches the switch detects for individual ACEs configured with the cnt (counter) option in an ACL assigned to the port by a RADIUS server.
show port-access authenticator clients detailed Command Output