The sequence of entries in an ACL is significant
When the switch uses an ACL to determine whether to permit or deny a packet, it compares the packet to the criteria specified in the individual ACEs in the ACL, beginning with the first ACE in the list and proceeding sequentially until a match is found. When a match is found, the switch applies the indicated action (permit or deny) to the packet. This is significant because, once a match is found for a packet, subsequent ACEs in the same ACL are not applied to that packet, regardless of whether they match the packet.
|
Line # |
Action |
|---|---|
|
n/a |
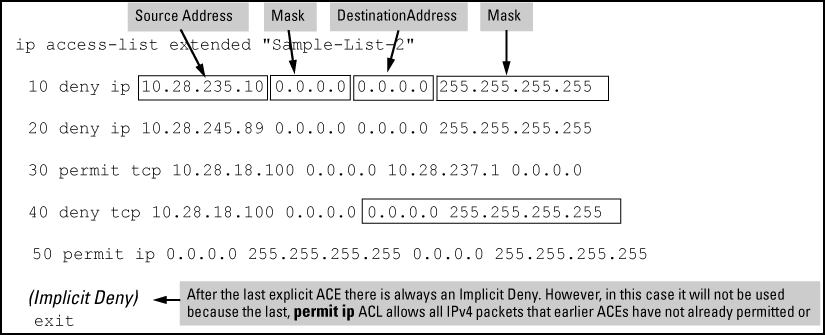
Shows type (extended) and ID (Sample-List-2). |
|
10 |
A packet from SA 10.28.235.10 is denied (dropped). This ACE filters out all packets received from 10.28.235.10. As a result, IPv4 traffic from that device is not allowed and packets from that device are not compared against any later entries in the list. |
|
20 |
A packet from SA 10.28.245.89 is denied (dropped). This ACE filters out all packets received from 10.28.245.89. As the result, IPv4 traffic from that device is not allowed and packets from that device are not compared against any later entries in the list. |
|
30 |
A TCP packet from SA 10.28.18.100 with a DA of 10.28.237.1 is permitted (forwarded). Since no earlier ACEs in the list have filtered TCP packets from 10.28.18.100 and destined for 10.28.237.1, the switch uses this ACE to evaluate such packets. Any packets that meet this criteria are forwarded. (Any packets that do not meet this TCP source-destination criteria are not affected by this ACE.) |
|
40 |
A TCP packet from source address 10.28.18.100 to any destination address is denied (dropped). Since, in this example, the intent is to block TCP traffic from 10.28.18.100 to any destination except the destination stated in the ACE at line 30, this ACE must follow the ACE at line 30. (If their relative positions were exchanged, all TCP traffic from 10.28.18.100 would be dropped, including the traffic for the 10.28.18.1 destination.) |
|
50 |
Any packet from any IPv4 SA to any IPv4 DA is permitted (forwarded). The only traffic to reach this ACE are IPv4 packets not specifically permitted or denied by the earlier ACEs. |
|
n/a |
The Implicit Deny is a function the switch automatically adds as the last action in all ACLs. It denies (drops) any IPv4 traffic from any source to any destination that has not found a match with earlier entries in the ACL. In this example, the ACE at line 50 permits (forwards) any IPv4 traffic not already permitted or denied by the earlier entries in the list, so there is no traffic remaining for action by the Implicit Deny function. |
|
exit |
Marks the end of the ACL. |