For a packet to be permitted, it must have a match with a "permit" ACE in all applicable ACLs assigned to an interface
On a given interface where multiple ACLs apply
to the same traffic, a packet having a match with a deny ACE
in any applicable ACL on the interface (including an implicit deny
any)is dropped.
Port A10 belongs to VLAN 100.
A static port ACL is configured on port A10.
A VACL is configured on VLAN 100.
An RACL is also configured for inbound, routed traffic on VLAN 100.
An inbound, switched packet entering on port
A10, with a destination on port A12, is screened by the static port
ACL and the VACL, regardless of a match with any permit or deny action.
A match with a deny action (including an implicit
deny) in either ACL causes the switch to drop the packet. (If the
packet has a match with explicit deny ACEs in multiple
ACLs and the log option is included in these ACEs, then a separate
log event occurs for each match.) The switched packet is not screened
by the RACL.
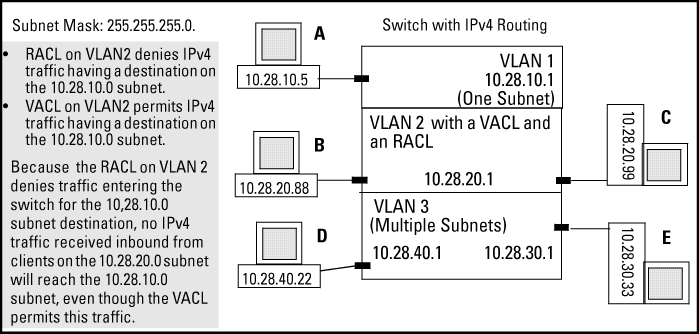
A VACL permitting traffic having a destination on the 10.28.10.0 subnet
An RACL that denies inbound traffic having a destination on the 10.28.10.0 subnet
In this case, no IPv4 traffic received on the
switch from clients on the 10.28.20.0 subnet reaches the 10.28.10.0
subnet, even though the VACL allows such traffic. This is because
the deny in the RACL causes the switch to drop
the traffic regardless of whether any other VACLs permit the traffic.