Possible scenarios for deployment
The following are examples of possible scenarios where LMA can be deployed.
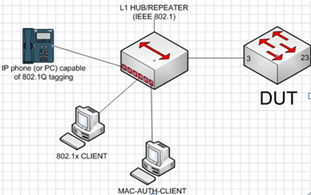
- In the following scenario multiple clients are connected to a hub that is tagged to vlan "A" and untagged to vlan "B". The hub is attached to a switch port that is tagged to vlan "A" and untagged to vlan "B". LMA authenticates clients and upon authentication places them in appropriate VLANs.
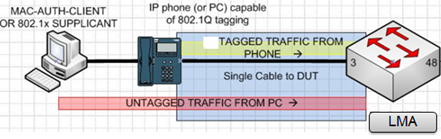
- In the following scenario, a client is daisy-chained to an IP Phone, which is connected to a tagged vlan port on a switch. The client is authenticating across an untagged vlan. When LMA is enabled on a port and the client connected to it fails to authenticate, the client is assigned attributes configured for the switch’s un-auth feature. If the client is authenticated, the switch overrides existing attributes with LMA attributes.