Features and benefits
Behavior-based operation that does not require identifying details unique to the code exhibiting the worm-like operation.
Handles unknown worms.
Needs no signature updates.
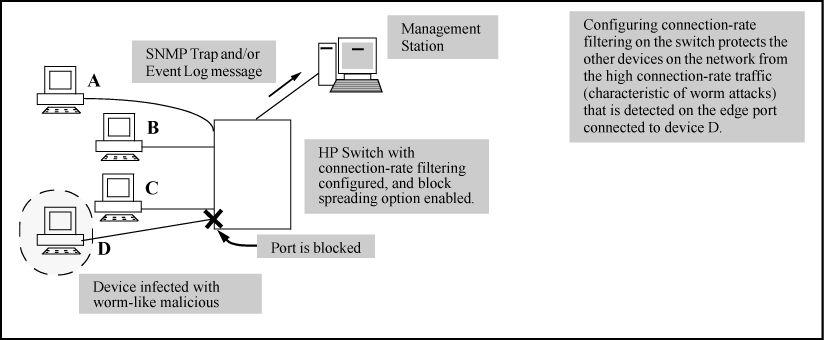
Protects network infrastructure by slowing or stopping IP traffic from hosts exhibiting high connection-rate behavior.
Allows network and individual switches to continue to operate, even when under attack.
Provides Event Log and SNMP trap warnings when worm-like behavior is detected.
Gives IT staff more time to react before the threat escalates to a crisis.
When configured on a port, connection-rate filtering is triggered by IPv4 traffic received inbound with a relatively high rate of IP connection attempts.
As stated previously, connection-rate filtering is triggered by inbound IP traffic exhibiting a relatively high-incidence of IP connection attempts from a single source.