Configuring the switch global RADIUS parameters
-
Number of login attempts: Specifies how many tries at entering the correct username and password pair are allowed before access is denied and the session terminated. Number of login attempts is a general
aaa authenticationparameter and is not specific to RADIUS. -
Global server key: The server key the switch uses for contacts with all RADIUS servers for which there is not a server-specific key configured by
radius-server host <ip-address> key <key-string>. This key is optional if you configure a server-specific key for each RADIUS server entered in the switch. -
Server timeout: Defines the time period in seconds for authentication attempts. If the timeout period expires before a response is received, the attempt fails.
-
Server dead time: Specifies the time in minutes during which the switch avoids requesting authentication from a server that has not responded to previous requests.
-
Retransmit attempts: If the first attempt to contact a RADIUS server fails, retransmit attempts specifies how many retries to allow the switch to attempt on that server.
-
Change of Authorization port: The
dyn-autz-portparameter specifies the UDP port number that listens for the Change of Authorization and Disconnect messages. The UDP port range is 1024-49151. The default port is 3799.
Syntax:
aaa authentication num-attempts <1-10>
Specifies how many tries for entering the correct username and password are allowed before shutting down the session due to input errors.
Default: 3; Range: 1–10.
[no] radius-server
key <global-key-string>
Specifies the global encryption key the switch uses with servers for which the switch does not have a server-specific key assignment. This key is optional if all RADIUS server addresses configured in the switch include a server-specific encryption key.
Default: Null.
[encrypted-key <global-key-string>]
Global encryption key, specified using a base64–encoded aes-256 encrypted string.
dead-time <1-1440>
Optional. Specifies the time in minutes during which the switch will not attempt to use a RADIUS server that has not responded to an earlier authentication attempt.
Default: 0; Range: 1–1440 minute
dyn-autz-port <1024-49151>
Specifies the UDP port number that listens for Change of Authorization or Disconnect messages. The range of ports is 1024–49151.
Default: 3799
radius-server timeout <1-15>
Specifies the maximum time the switch waits for a response to an authentication request before counting the attempt as a failure.
Default: 5 seconds; Range: 1–15 seconds
radius-server retransmit <1-5>
If a RADIUS server fails to respond to an authentication request, specifies how many retries to attempt before closing the session.
Default: 3; Range: 1–5
To calculate RADIUS timeout value, use equation:
((radius-server retransmit + 1) * radius-server timeout)*number of RADIUS servers configured)
If three RADIUS servers are configured with default values of
radius-server timeout and
radius-server retransmit, the RADIUS timeout value will be ((3+1)*5)*3 = 60 seconds.
To apply secondary authentication methods (authorized or cached reauthentication) successfully, radius-server timeout value (as per the equation) must be lesser than the server-timeout value. If radius-server timeout value is higher than the server timeout value, the client will be placed in
timed out-unauth vlan
(if
unauth-vid is configured) or timed out-no vlan state after trying for max-requests(default value is 3).
Where the switch has multiple RADIUS servers configured to support authentication requests, if the first server fails to respond, then the switch tries the next server in the list, and so-on. If none of the servers respond, then the switch attempts to use the secondary authentication method configured for the type of access being attempted (console, Telnet, or SSH). For more information, see the Troubleshooting chapter of the management and configuration guide for your switch.
Example:
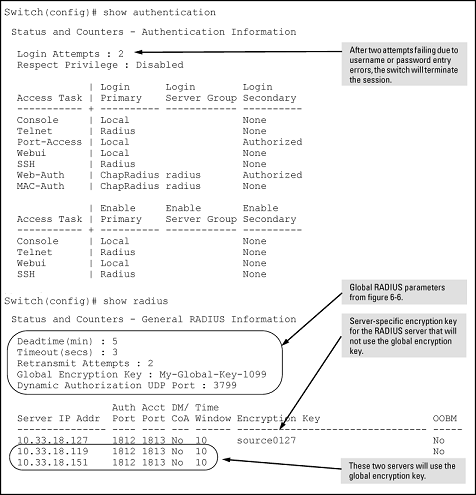
Suppose that your switch is configured to use three RADIUS servers for authenticating access through Telnet and SSH. Two of these servers use the same encryption key. In this case the plan is to configure the switch with the following global authentication parameters:
-
Allow only two tries to correctly enter username and password.
-
Use the global encryption key to support the two servers that use the same key. (For this example, assume that you did not configure these two servers with a server-specific key.)
-
Use a dead time of five minutes for a server that fails to respond to an authentication request.
-
Allow three seconds for request timeouts.
-
Allow two retries following a request that did not receive a response.
Global configuration exercise for RADIUS authentication
switch(config)# aaa authentication num-attempts 2 switch(config)# radius-server key My-Global-KEY-1099 switch(config)# radius-server dead-time 5 switch(config)# radius-server timeout 3 switch(config)# radius-server retransmit 2 switch(config)# write mem