Assigning time-dependent keys to a chain
A time-dependent key has Accept or Send time constraints. It is valid only during the times that are defined for the key . If a time-dependent key is used, there is usually more than one key in the key chain entry.
Syntax:
[no]key-chain <chain_name> key <key_id>
Generates or deletes a key in the key chain entry
<chain_name>
. Using the optional
no form of the command deletes the key. The
<key_id>
is any number from 0-255.
[key-string <key_str>]
This option specifies the key value referenced by the protocol using the key. The
<key_str>
can be any string up to 14 characters in length.
[encrypted-key <key_str>]
Set key string using a base64-encoded aes-256 encrypted string.
accept-lifetime <mm/dd/yy[yy]hh:mm:ss|now>
Specifies the start date and time of the valid period in which the switch can use this key to authenticate inbound packets.
duration <mm/dd/yy[yy]hh:mm:ss|seconds>
Specifies the
time period during which the switch can use this key to authenticate inbound packets. Duration is either an end date and time or the number of seconds to allow after the start date and time ( which is the
accept-lifetime setting).
send-lifetime <mm/dd/yy[yy]hh:mm:ss|now>
Specifies the start date and time of the valid period in which the switch can transmit this key as authentication for outbound packets.
show key-chain <chain_name>
Displays the detail information about the keys used in the key chain named <chain_name
>.
Using time-dependent keys requires that all the switches have accurate, synchronized time settings. You can manually set the time or use the Time protocol feature included in the switches. See time protocols in the management and configuration guide for your switch.
Example:
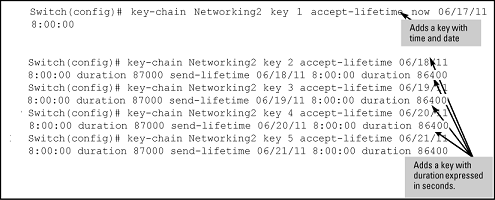
Given transmission delays and the variations in the time value from switch to switch, it is advisable to include some flexibility in the Accept lifetime of the keys you configure. Otherwise, the switch may disregard some packets because either their key has expired while in transport or there are significant time variations between switches.
To list the result of the commands in Adding time-dependent keys to a key chain entry:

Use
show key-chain to display the key status at the time the command is issued. Using the information from the example configuration in
Adding time-dependent keys to a key chain entry and
Display of time-dependent keys in the key chain entry if you execute
show key-chain at 8:05 on 01/19/03, the display would appear as follows:
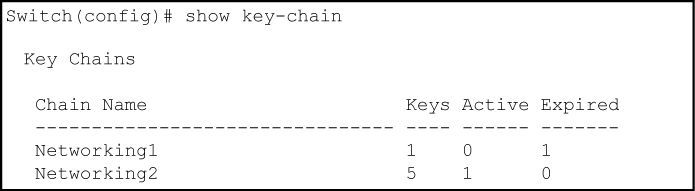
The "Networking1" key chain entry is a time-independent key and will not expire. "Networking2" uses time-dependent keys, which result in this data:
|
Expired=1 |
Key 1 has expired because its lifetime ended at 8:10 on 01/18/03, the previous day. |
|
Active=2 |
Key 2 and 3 are both active for 10 minutes from 8:00 to 8:10 on 1/19/03. |
Keys 4 and 5 are either not yet active or expired. The total number of keys is 5.