Enabling ACL logging on the switch
Procedure
-
If you are using a syslog server, use the
logging <ip–addr>command to configure the syslog server IP addresses; ensure that the switch can access any syslog servers you specify. -
Use
logging facility syslogto enable the logging for syslog operation. -
Use the
debug destinationcommand to configure one or more log destinations. -
Destination options include
loggingandsession. For more information on debug, see "debug and syslog messaging operation" in the latest management and configuration guide for your switch. -
Use
debug aclordebug allto configure the debug operation to include ACL messages. -
Configure an ACL with the
denyaction and thelogoption in one or more ACEs.
-
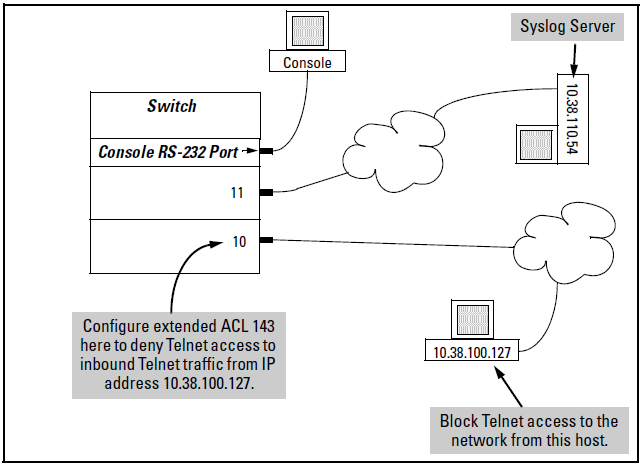
On port 10, configure an extended ACL with an ACL-ID of 143 to deny Telnet traffic from IP address 10.38.100.127.
-
Configure the switch to send an ACL log message to the console and to a Syslog server at IP address 10.38.110.54 on port 11 if the switch detects a match denying Telnet access from 10.38.100.127.
Commands for applying an ACL with logging:
Switch(config)# access-list 143 deny tcp host 10.38.100.127 any eq telnet log Switch(config)# access-list 143 permit ip any any Switch(config)# interface 10 access–group 143 in Switch(config)# logging 10.38.110.54 Switch(config)# debug ac1 Switch(config)# debug destination logging Switch(config)# debug destination session Switch(config)# write memory Switch(config)# show debug Debug Logging Destination: Logging 10.38.110.54 Session Enabled debug types: event acl log